Security News > 2023 > April

In this article, we'll explore the evolution of password policies, from basic to advanced, and discuss the key factors in creating a robust password policy, including password length, complexity, and the use of custom dictionaries. We'll also look at common password practices to avoid, the risks associated with password reuse, and the role of education in password security.

A little-known Russian-speaking cyber-espionage group has been linked to a new politically-motivated surveillance campaign targeting high-ranking government officials, telecom services, and public service infrastructures in Tajikistan. The intrusion set, dubbed Paperbug by Swiss cybersecurity company PRODAFT, has been attributed to a threat actor known as Nomadic Octopus.

As a first step, our report recommends the inclusion of AI security concerns within the cybersecurity programs of developers and users. Many AI products are deployed without institutions fully understanding the security risks they pose.

RSA Conference 2023 is taking place at the Moscone Center in San Francisco. Check out our microsite for the conference for all the most important news.

Interestingly, LimeRAT shares similarities with njRAT, which ANY.RUN ranks as the third most popular malware family in terms of uploads during Q1 2023. ANY.RUN researchers have recently conducted an in-depth analysis of a LimeRAT sample and successfully extracted its configuration.

RSA Conference 2023 is taking place at the Moscone Center in San Francisco. Check out our microsite for the conference for all the most important news.

Clop and LockBit ransomware affiliates are behind the recent attacks exploiting vulnerabilities in PaperCut application servers, according to Microsoft and Trend Micro researchers."Microsoft is attributing the recently reported attacks exploiting the CVE-2023-27350 and CVE-2023-27351 vulnerabilities in print management software PaperCut to deliver Clop ransomware to the threat actor tracked as Lace Tempest," Microsoft shared.
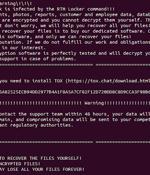
The threat actors behind RTM Locker have developed a ransomware strain that's capable of targeting Linux machines, marking the group's first foray into the open source operating system. "Its locker ransomware infects Linux, NAS, and ESXi hosts and appears to be inspired by Babuk ransomware's leaked source code," Uptycs said in a new report published Wednesday.

GitHub has announced that its private vulnerability reporting feature for open source repositories is now available to all project owners. The private vulnerability reporting feature provides a direct collaboration channel that allows researchers to more easily report vulnerabilities, and maintainers to easily fix them.

Microsoft has confirmed that the active exploitation of PaperCut servers is linked to attacks designed to deliver Cl0p and LockBit ransomware families. The tech giant's threat intelligence team is attributing a subset of the intrusions to a financially motivated actor it tracks under the name Lace Tempest, which overlaps with other hacking groups like FIN11, TA505, and Evil Corp. "In observed attacks, Lace Tempest ran multiple PowerShell commands to deliver a TrueBot DLL, which connected to a C2 server, attempted to steal LSASS credentials, and injected the TrueBot payload into the conhost.exe service," Microsoft said in a series of tweets.