Security News > 2023 > March

In brief Cybersecurity and Infrastructure Security Agency's director Jen Easterly has been outspoken in her drive to bring more women into the security industry, and this year for International Women's Day her agency formalized that pledge by announcing a partnership with nonprofit Women in CyberSecurity. The US department of Homeland Security agency and WiCyS signed a memorandum of understanding on Wednesday to help raise awareness of job opportunities for women in cybersecurity and build "a pipeline for the next generation of women" able to fill those roles, the agency said.
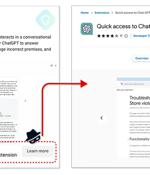
A fake ChatGPT-branded Chrome browser extension has been found to come with capabilities to hijack Facebook accounts and create rogue admin accounts, highlighting one of the different methods cyber criminals are using to distribute malware. "By hijacking high-profile Facebook business accounts, the threat actor creates an elite army of Facebook bots and a malicious paid media apparatus," Guardio Labs researcher Nati Tal said in a technical report.

While NIST hasn't directly developed standards related to securing the SaaS ecosystem, they are instrumental in the way we approach SaaS security. They need to integrate seamlessly with SaaS applications and provide coverage for the entire SaaS stack.

TechRepublic Premium Business continuity policy PURPOSE The purpose of this policy is to provide guidelines for establishing and following appropriate business continuity requirements. This policy can be customized as needed to fit the needs of your organization.
Threat actors have been increasingly observed using AI-generated YouTube Videos to spread a variety of stealer malware such as Raccoon, RedLine, and Vidar. "The videos lure users by pretending to be tutorials on how to download cracked versions of software such as Photoshop, Premiere Pro, Autodesk 3ds Max, AutoCAD, and other products that are licensed products available only to paid users," CloudSEK researcher Pavan Karthick M said.

Let's start with a couple of plums from the US, where - hold onto your peaked caps - law enforcement officials have been breaking the law, wholesale. The government says, with a straight face, that to Protect the Children it must install back doors in end-to-end encryption.

In this article, I'll outline another kind of risk posed by the event: the huge opportunity this frenzy around SVB presents for cyber attackers, and the cyber risk this creates for thousands of SVB account holders, and their customers and suppliers. SVB customers now make perfect marks for phishing and fraud attacks.

Webinar It's like living in a fever dream out there in the world of cybersecurity. More and more sophisticated attacks, a tsunami of solutions offering a gilt-edged escape from the need to constantly reconfigure your defences, and relentless pressure to always stay one step ahead of the hackers.

India's government has started to consult some proposed details of its long-awaited Digital India Act, including a declaration that the bill needed a dedicated adjudicatory tool for offenses committed online. According to the Ministry of Electronics & IT, minister of state Rajeev Chandrasekhar said the bill's guiding principles include "Managing the complexities of internet and rapid expansion of the types of intermediaries addressing the risks of emerging technologies, protecting citizen rights, managing and setting guardrails for the varied intermediaries on the internet."

More than a dozen security flaws have been disclosed in E11, a smart intercom product made by Chinese company Akuvox. "The vulnerabilities could allow attackers to execute code remotely in order to activate and control the device's camera and microphone, steal video and images, or gain a network foothold," Claroty security researcher Vera Mens said in a technical write-up.