Security News > 2023 > February

Citrix Systems has released security updates for vulnerabilities in its Virtual Apps and Desktops, and Workspace Apps products. Citrix products are widely used by organizations worldwide, so it's critical to apply the available security updates to prevent intruders from having an easy way to escalate their privileges on breached systems.

Automakers Hyundai and KIA are rolling out an emergency software update on several of their car models impacted by an easy hack that makes it possible to steal them."In response to increasing thefts targeting its vehicles without push-button ignitions and immobilizing anti-theft devices in the United States, Hyundai is introducing a free anti-theft software upgrade to prevent the vehicles from starting during a method of theft popularized on TikTok and other social media channels," reads Hyundai's announcement.

You might not think about it, but securing your iOS device can help protect your personal information if you lose your device or leave it unattended. The best way to secure your iOS device is to add a passcode.

A hacker is using fake code-signing certificates impersonating cybersecurity firm Emsisoft to target customers using its security products, hoping to bypass their defenses. In a new security advisory, Emsisoft warned that one of its customers was targeted by hackers using an executable signed by a spoofed Emsisoft certificate.

Oakland has declared a local state of emergency because of the impact of a ransomware attack that forced the City to take all its IT systems offline on February 8th. Interim City Administrator G. Harold Duffey declared a state of emergency to allow the City of Oakland to expedite orders, materials and equipment procurement, and activate emergency workers when needed."Today, Interim City Administrator, G. Harold Duffey issued a local state of emergency due to the ongoing impacts of the network outages resulting from the ransomware attack that began on Wednesday, February 8," a statement issued today reads.

Protecting this account from phishing, or brute-force password attempts through a strong password policy, will keep a threat actor from accessing your company's password vaults. NIST recommends checking passwords against a breached password list.
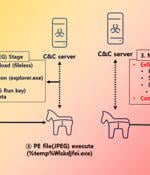
The North Korea-linked threat actor tracked as APT37 has been linked to a piece of new malware dubbed M2RAT in attacks targeting its southern counterpart, suggesting continued evolution of the group's features and tactics. APT37, also tracked under the monikers Reaper, RedEyes, Ricochet Chollima, and ScarCruft, is linked to North Korea's Ministry of State Security unlike the Lazarus and Kimsuky threat clusters that are part of the Reconnaissance General Bureau.

While the Twitter outage affected comparatively few Twitter users, it could hold a larger message about the dangers not just to operations but also security for organizations mulling big cuts in workforce. With just 1,300 active staff, Twitter now has 80% fewer workers than the roughly 8,000 the company had on its payroll before the October 2022 takeover by Elon Musk, by some reports.

Digital communication would not be possible without file sharing. Whether we are opening an exported Excel file with a Salesforce report or downloading a new note taking software, we are using files to share information and perform critical tasks.

A new financially motivated campaign that commenced in December 2022 has seen the unidentified threat actor behind it deploying a novel ransomware strain dubbed MortalKombat and a clipper malware known as Laplas. The starting point that kicks off the multi-stage attack chain is a phishing email bearing a malicious ZIP file that's used as a pathway to deliver either the clipper or the ransomware.