Security News > 2023 > January

Porsche cut its minting of a new NFT collection short after a dismal turnout and backlash from the crypto community, allowing threat actors to fill the void by creating phishing sites that steal digital assets from cryptocurrency wallets. To make matters worse, a flourishing NFT resale market was set up over at OpenSea, where it was cheaper to buy the Porsche collectibles than get the original, which devalued the assets immediately and further infuriated investors and traders.

Users of enterprise-managed Chromebooks now, for better or worse, have a way to break the shackles of administrative control through an exploit called SHI1MMER. SH1MMER - you may pronounce the "1" as an "i" - is a shim exploit, or more specifically, a weaponized Return Merchandise Authorization shim. A shim is Google-signed software used by hardware service vendors for Chromebook diagnostics and repairs.

The development team behind the open-source password management software KeePass is disputing what is described as a newly found vulnerability that allows attackers to stealthily export the entire database in plain text. The new vulnerability is now tracked as CVE-2023-24055, and it enables threat actors with write access to a target's system to alter the KeePass XML configuration file and inject a malicious trigger that would export the database, including all usernames and passwords in cleartext.

Malware developers and penetration testers are in high demand across dark web job posting sites, with a few astonishing - but mostly average - wages. The report found that many ads mirror the style of legitimate IT job postings but with a couple big exceptions: all the work is remote by default, and - for obvious reasons - there are no formal employment contracts for these illegal gigs.

Cybercrime groups are increasingly running their operations as a business, promoting jobs on the dark web that offer developers and hackers competitive monthly salaries, paid time off, and paid sick leaves. In a new report by Kaspersky, which analyzed 200,000 job ads posted on 155 dark websites between March 2020 and June 2022, hacking groups and APT groups seek to hire mainly software developers, offering very competitive packages to entice them.
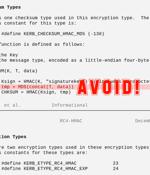
Astonishingly, the CVE-2022-38023 vulnerability existed in the first place because both Windows and Samba still supported a style of integrity protection based on the long-deprecated hashing algorithm MD5. Simply put, network authentication using Microsoft's version of the Kerberos protocol still allowed data to be integrity-protected using flawed cryptography. Assuming a reliable algorithm, with no exploitable weaknesses, you'd expect that a hash with X bits of output would need about 2X-1 tries to find a second input that collided with the hash of an existing file.

Researchers with Google-owned security shop Mandiant started seeing significant changes to the Gootloader malware package - also known as Gootkit - in November 2022, including using multiple variations of FONELAUNCH, a.NET-based loader, as well as some newly developed payloads and obfuscation techniques. A Gootloader infection starts via a search engine optimization poisoning attack, with a victim who is searching online for business-related documents, such as templates, agreements, or contracts, being lured into going to a website compromised by the criminal gang.

GitHub says unknown attackers have stolen encrypted code-signing certificates for its Desktop and Atom applications after gaining access to some of its development and release planning repositories. GitHub has found no evidence that the password-protected certificates were used for malicious purposes.

QNAP is warning customers to install QTS and QuTS firmware updates that fix a critical security vulnerability allowing remote attackers to inject malicious code on QNAP NAS devices. "A vulnerability has been reported to affect QNAP devices running QTS 5.0.1 and QuTS hero h5.0.1. If exploited, this vulnerability allows remote attackers to inject malicious code,' warns the QNAP security advisory."

UK sports apparel chain JD Sports is warning customers of a data breach after a server was hacked that contained online order information for 10 million customers. JD Sports says it detected the unauthorized access immediately and responded quickly to secure the breached server, preventing subsequent access attempts.