Security News > 2022 > September > Researchers Disclose Critical Vulnerability in Oracle Cloud Infrastructure
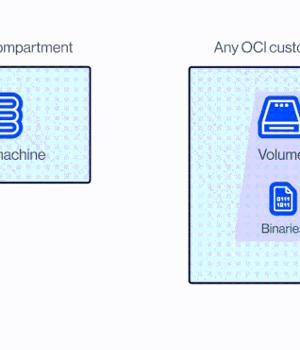
Researchers have disclosed a new severe Oracle Cloud Infrastructure vulnerability that could be exploited by users to access the virtual disks of other Oracle customers.
"Each virtual disk in Oracle's cloud has a unique identifier called OCID," Shir Tamari, head of research at Wiz, said in a series of tweets.
"Given the OCID of a victim's disk that is not currently attached to an active server or configured as shareable, an attacker could 'attach' to it and obtain read/write over it," Tamari added.
The cloud security firm, which dubbed the tenant isolation vulnerability "AttachMe," said Oracle patched the issue within 24 hours of responsible disclosure on June 9, 2022.
At its core, the vulnerability is rooted in the fact that a disk could be attached to a compute instance in another account via the Oracle Cloud Identifier without any explicit authorization.
"Insufficient validation of user permissions is a common bug class among cloud service providers," Wiz researcher Elad Gabay said.
News URL
https://thehackernews.com/2022/09/researchers-disclose-critical.html
Related news
- US charges Chinese hackers linked to critical infrastructure breaches (source)
- Elastic Releases Urgent Fix for Critical Kibana Vulnerability Enabling Remote Code Execution (source)
- Moxa Issues Fix for Critical Authentication Bypass Vulnerability in PT Switches (source)
- Critical PHP RCE vulnerability mass exploited in new attacks (source)
- CISA: Medusa ransomware hit over 300 critical infrastructure orgs (source)
- New Critical AMI BMC Vulnerability Enables Remote Server Takeover and Bricking (source)
- IBM scores perfect 10 ... vulnerability in mission-critical OS AIX (source)
- Critical Veeam Backup & Replication RCE vulnerability fixed, patch ASAP! (CVE-2025-23120) (source)
- Infoseccers criticize Veeam over critical RCE vulnerability and a failing blacklist (source)
- UAT-5918 Targets Taiwan's Critical Infrastructure Using Web Shells and Open-Source Tools (source)