Security News > 2022 > June

Security researchers at Intezer and BlackBerry have documented Symbiote, a wholly unique, multi-purpose piece of Linux malware that is nearly impossible to detect. "What makes Symbiote different from other Linux malware that we usually come across, is that it needs to infect other running processes to inflict damage on infected machines. Instead of being a standalone executable file that is run to infect a machine, it is a shared object library that is loaded into all running processes using LD PRELOAD, and parasitically infects the machine," the researchers pointed out.

Kinsta vs WP Engine: Managed WordPress hosting comparison We may be compensated by vendors who appear on this page through methods such as affiliate links or sponsored partnerships. WP Engine is the biggest name in WordPress hosting, but Kinsta is quickly establishing itself as a worthy competitor.

Conducted by The Enterprise Strategy Group, which surveyed 1,000 IT and security professionals in eight countries, a new Illumio report discovered that 47% of security leaders do not believe they will be breached despite increasingly sophisticated and frequent attacks, broad adoption of zero trust technologies, and the proven business and security impact of zero trust segmentation, which isolates machines across the hybrid attack surface to stop breaches from spreading. In the past two years alone, 76% of organizations surveyed have been attacked by ransomware and 66% have experienced at least one software supply chain attack.

The criminals behind the Emotet botnet - which rose to fame as a banking trojan before evolving into spamming and malware delivery - are now using it to target credit card information stored in the Chrome web browser."The notorious botnet Emotet is back, and we can expect that new tricks and evasion techniques will be implemented in the malware as the operation progresses, perhaps even returning to being a significant global threat," Ron Ben Yizhak, security researcher with cybersecurity vendor Deep Instinct, wrote in a blog post in November outlining the technical evolutions in the malware.
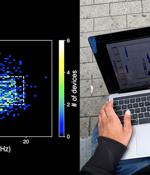
A new research undertaken by a group of academics from the University of California San Diego has revealed for the first time that Bluetooth signals can be fingerprinted to track smartphones. "To perform a physical-layer fingerprinting attack, the attacker must be equipped with a Software Defined Radio sniffer: a radio receiver capable of recording raw IQ radio signals," the researchers said in a new paper titled "Evaluating Physical-Layer BLE Location Tracking Attacks on Mobile Devices."

Cybersecurity researchers have taken the wraps off what they call a "Nearly-impossible-to-detect" Linux malware that could be weaponized to backdoor infected systems. Dubbed Symbiote by threat intelligence firms BlackBerry and Intezer, the stealthy malware is so named for its ability to conceal itself within running processes and network traffic and drain a victim's resources like a parasite.

The notorious Emotet malware has turned to deploy a new module designed to siphon credit card information stored in the Chrome web browser. The credit card stealer, which exclusively singles out Chrome, has the ability to exfiltrate the collected information to different remote command-and-control servers, according to enterprise security company Proofpoint, which observed the component on June 6.

May 2022 Patch Tuesday provided the final releases for several Windows 10 operating systems and this month we'll see the final update for Internet Explorer 11. June 2022 Patch Tuesday forecast We hope to see a fix for CVE-2022-30190 in this month's operating systems updates.

RSA Conference 2022 is underway at the Moscone Center in San Francisco. Check out our microsite for the conference for all the most important news.

Threat researcher Joey Chen of Sentinel Labs says he's spotted a decade worth of cyber attacks he's happy to attribute to a single Chinese gang. Chen has named the group Aoqin Dragon, says its goal is espionage, and that it prefers targets in Australia, Cambodia, Hong Kong, Singapore, and Vietnam.