Security News > 2021

A piece of malware linked by U.S. intelligence agencies to hackers believed to be backed by the Russian government remains a mystery to the private sector, which apparently hasn't found a single sample of the malware, and one researcher went as far as suggesting that it may be a false flag set up by the United States itself. In August 2020, the NSA and the FBI released a joint cybersecurity advisory detailing a piece of malware they named Drovorub.

Even with the security updates prompted by the recent SolarWinds Orion supply-chain attack, researchers still found some glaring vulnerabilities affecting the platform, one of them allowing code execution with top privileges. The vulnerabilities have been discovered and reported to SolarWinds by Martin Rakhmanov, Security Research Manager, SpiderLabs at Trustwave, and have proof-of-concept exploit code available.

A recently discovered heap-based buffer overflow vulnerability in Linux SUDO also impacts the latest version of Apple macOS Big Sur, with no patch available yet. Last week, BleepingComputer had reported on CVE-2021-3156 aka Baron Samedit, a flaw in SUDO which lets local users gain root privileges.

The most severe of these could allow trivial remote code execution with high privileges. The most critical bug does not require local access and allows complete control over SolarWinds Orion remotely without having any credentials at all.

Apps that tracked and sold people's whereabouts were more prevalent than perhaps first thought. A report out today has identified 450 Android apps downloaded 1.7 billion times that used SDKs to track the location of smartphones.

Vulnerability intelligence-as-a-service outfit vFeed has compiled a list of the top 10 most exploited vulnerabilities from 2020, and among them are SMBGhost, Zerologon, and SIGRed. What is vFeed?...

To limit the impact of zero-day vulnerabilities, Google security researcher Maddie Stone would like those developing software fixes to stop delivering shoddy patches. "Looking at them all together as a group, the number that stuck out the most to me was that six out of the 24 zero-days exploited in 2020 are variants of previously disclosed vulnerabilities," she said.

An online community promoting female escorts and reviews of their services has suffered a data breach after a hacker downloaded the site's database. The site is very active with over 2.4 million topics, 12.5 million posts, and over 470,000 members.
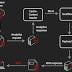
New details have emerged about a vast network of rogue extensions for Chrome and Edge browsers that were found to hijack clicks to links in search results pages to arbitrary URLs, including phishing sites and ads. Collectively called "CacheFlow" by Avast, the 28 extensions in question - including Video Downloader for Facebook, Vimeo Video Downloader, Instagram Story Downloader, VK Unblock - made use of a sneaky trick to mask its true purpose: Leverage Cache-Control HTTP header as a covert channel to retrieve commands from an attacker-controlled server.

Your company's vendor management program may not be what you need to get the most out of your cybersecurity vendors, so I'll focus on a Cyber Vendor Optimization Strategy. Depending on which vendor you're dealing with, what you share about your challenges and how you leverage the vendor could be completely different things.