Security News > 2021 > December

Cryptocurrency users in Ethiopia, Nigeria, India, Guatemala, and the Philippines are being targeted by a new variant of the Phorpiex botnet called Twizt that has resulted in the theft of virtual coins amounting to $500,000 over the last one year. Israeli security firm Check Point Research, which detailed the attacks, said the latest evolutionary version "Enables the botnet to operate successfully without active servers," adding it supports no less than 35 wallets associated with different blockchains, including Bitcoin, Ethereum, Dash, Dogecoin, Litecoin, Monero, Ripple, and Zilliqa, to facilitate crypto theft.

Web infrastructure company Cloudflare on Wednesday revealed that threat actors are actively attempting to exploit a second bug disclosed in the widely used Log4j logging utility, making it imperative that customers move quickly to install the latest version as a barrage of attacks continues to pummel unpatched systems with a variety of malware. Even more troublingly, researchers at security firm Praetorian warned of a third separate security weakness in Log4j version 2.15.0 that can "Allow for exfiltration of sensitive data in certain circumstances." Additional technical details of the flaw have been withheld to prevent further exploitation, but it's not immediately clear if this has been already addressed in version 2.16.0.

Some threat actors exploiting the Apache Log4j vulnerability have switched from LDAP callback URLs to RMI or even used both in a single request for maximum chances of success. From LDAP to RMI. Most attacks targeting the Log4j "Log4Shell" vulnerability have been through the LDAP service.

Some threat actors exploiting the Apache Log4j vulnerability have switched from LDAP callback URLs to RMI or even used both in a single request for maximum chances of success. From LDAP to RMI. Most attacks targeting the Log4j "Log4Shell" vulnerability have been through the LDAP service.

Facebook has disrupted the operations of seven different spyware-making companies, blocking their Internet infrastructure, sending cease and desist letters, and banning them from its platform. "As a result of our months-long investigation, we took action against seven different surveillance-for-hire entities to disrupt their ability to use their digital infrastructure to abuse social media platforms and enable surveillance of people across the internet," said Director of Threat Disruption David Agranovich and Head of Cyber Espionage Investigations Mike Dvilyanski.

Portland brewery and hotel chain McMenamins suffered a Conti ransomware attack over the weekend that disrupted the company's operations. The ransomware attack occurred over the weekend, on December 12th, with sources telling BleepingComputer that the Conti gang conducted it.

Cloudflare is experiencing "Wide-spread" latency issues with their network and services, causing websites to load slowly and customers to experience performance issues accessing the customer dashboard. The issues started at around 3 PM EST and affect sites worldwide, including BleepingComputer.

If you've just started climbing the IT professional career ladder or recently learned a little basic coding, you can quickly turn your experience into lucrative cybersecurity skills for a career upgrade. With cyber crimes becoming more plentiful and causing more widespread damage, demand for cybersecurity skills is skyrocketing.
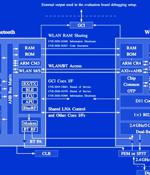
Cybersecurity researchers have demonstrated a new attack technique that makes it possible to leverage a device's Bluetooth component to directly extract network passwords and manipulate traffic on a Wi-Fi chip. The novel attacks work against the so-called "Combo chips," which are specialized chips that are equipped to handle different types of radio wave-based wireless communications, such as Wi-Fi, Bluetooth, and LTE. "We provide empirical evidence that coexistence, i.e., the coordination of cross-technology wireless transmissions, is an unexplored attack surface," a group of researchers from the Technical University of Darmstadt's Secure Mobile Networking Lab and the University of Brescia said in a new paper.

They've been an active threat group since 2011, but a recent uptick in activity from Earth Centaur - previously known as Tropic Trooper - aimed specifically at transportation and government agencies is setting off alarm bells among experts. The analysts were able to attribute the new Earth Centaur activity to Tropic Trooper after finding similar code in configuration decoding, they reported.