Security News > 2021 > August

On Thursday, a 21-year-old US citizen claiming to be the attacker who stole data on more than 50 million T-Mobile customers called the telecom's security "Awful." As of Aug. 18, T-Mobile had estimated the total number of ripped-off records to be ~40 million: a number that rose to ~50 million on Aug. 20 and could double if the purported thief is true to his word.

Microsoft announced a new Microsoft 365 Widget in the latest Windows 11 Dev build released for Windows Insiders in the Dev and Beta Channels. Windows 11's new widget provides quicker access to frequently opened files and more for all Insiders in the Dev and Beta channels who install Windows 11 Preview build 22000.
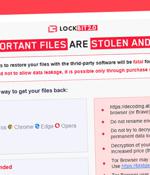
A new ransomware family that emerged last month comes with its own bag of tricks to bypass ransomware protection by leveraging a novel technique called "Intermittent encryption." Called LockFile, the operators of the ransomware have been found exploiting recently disclosed flaws such as ProxyShell and PetitPotam to compromise Windows servers and deploy file-encrypting malware that scrambles only every alternate 16 bytes of a file, thereby giving it the ability to evade ransomware defences.
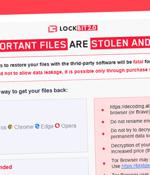
A new ransomware family that emerged last month comes with its own bag of tricks to bypass ransomware protection by leveraging a novel technique called "Intermittent encryption." Called LockFile, the operators of the ransomware have been found exploiting recently disclosed flaws such as ProxyShell and PetitPotam to compromise Windows servers and deploy file-encrypting malware that scrambles only every alternate 16 bytes of a file, thereby giving it the ability to evade ransomware defences.
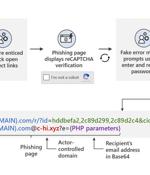
Microsoft is warning of a widespread credential phishing campaign that leverages open redirector links in email communications as a vector to trick users into visiting malicious websites while effectively bypassing security software. "Attackers combine these links with social engineering baits that impersonate well-known productivity tools and services to lure users into clicking," Microsoft 365 Defender Threat Intelligence Team said in a report published this week.

Google and Microsoft said they are pledging to invest a total of $30 billion in cybersecurity advancements over the next five years, as the U.S. government partners with private sector companies to address threats facing the country in the wake of a string of sophisticated malicious cyber activity targeting critical infrastructure, laying bare the risks to data, organizations, and governments worldwide. Microsoft will invest $20 billion over the next five years to deliver advanced security solutions, in addition to making available $150 million in technical services to help federal, state, and local governments with upgrading security protections.

Google and Microsoft said they are pledging to invest a total of $30 billion in cybersecurity advancements over the next five years, as the U.S. government partners with private sector companies to address threats facing the country in the wake of a string of sophisticated malicious cyber activity targeting critical infrastructure, laying bare the risks to data, organizations, and governments worldwide. To that end, the U.S. government on Wednesday announced a collaboration between the National Institute of Standards and Technology and industry partners to develop a new framework to improve the security and integrity of the technology supply chain, alongside plans to expand the Industrial Control Systems Cybersecurity Initiative to secure natural gas pipelines.

Microsoft has warned that it has been tracking a widespread credential-phishing campaign that relies on open redirector links, while simultaneously suggesting it can defend against such schemes. Microsoft says that open redirects have legitimate uses, pointing to the way sales and marketing campaigns rely on them to lead customers to specific landing pages and to gather web metrics.

It’s pretty. As usual, you can also use this squid post to talk about the security stories in the news that I haven’t covered. Read my blog posting guidelines here.

The makers of Parallels Desktop has released a workaround fix for a high-severity privilege escalation bug that impacts its Parallels Desktop 16 for Mac software and all older versions. Parallels Desktop, now owned by private equity giant KKR, is used by seven million users, according to the company, and allows Mac users to run Windows, Linux and other operating systems on their macOS. The vulnerability allows malicious software running in a Parallels virtual machine to access macOS files shared in a default configuration of the software.