
New Mirai botnet infect TBK DVR devices via command injection flaw
A new variant of the Mirai malware botnet is exploiting a command injection vulnerability in TBK...

New Supply Chain Malware Operation Hits npm and PyPI Ecosystems, Targeting Millions Globally
Cybersecurity researchers have flagged a supply chain attack targeting over a dozen packages...

Enterprises are getting stuck in AI pilot hell, say Chatterbox Labs execs
Security, not model performance, is what's stalling adoption Interview Before AI becomes...
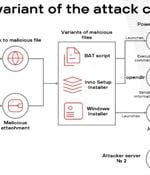
Malicious Browser Extensions Infect Over 700 Users Across Latin America Since Early 2025
Cybersecurity researchers have shed light on a new campaign targeting Brazilian users since the...

Week in review: Google fixes exploited Chrome zero-day, Patch Tuesday forecast
Here’s an overview of some of last week’s most interesting news, articles, interviews and...

Malware found in NPM packages with 1 million weekly downloads
A significant supply chain attack hit NPM after 15 popular Gluestack packages with over 950,000...

Malicious npm packages posing as utilities delete project directories
Two malicious packages have been discovered in the npm JavaScript package index, which...
Vulnerabilities by Risk level (Last 12 months)
Vulnerabilities by Vendor (Last 12 months)
Latest Vulnerabilities
-
CVE-2025-5839
8.8A vulnerability, which was classified as critical, has been found in Tenda AC9 15.03.02.13. Affected by this issue is the function fromadvsetlanip of the file /goform/AdvSetLanip of the component...
-
CVE-2025-5840
7.3A vulnerability, which was classified as critical, was found in SourceCodester Client Database Management System 1.0. This affects an unknown part of the file /user_update_customer_order.php. The...
-
CVE-2025-5838
6.3A vulnerability classified as critical was found in PHPGurukul Employee Record Management System 1.3. Affected by this vulnerability is an unknown functionality of the file...
-
CVE-2025-5836
6.3A vulnerability was found in Tenda AC9 15.03.02.13. It has been rated as critical. This issue affects the function formSetIptv of the file /goform/SetIPTVCfg of the component POST Request Handler....
-
CVE-2025-5837
6.3A vulnerability classified as critical has been found in PHPGurukul Employee Record Management System 1.3. Affected is an unknown function of the file /admin/allemployees.php. The manipulation of...
Latest Critical Vulnerabilities
-
CVE-2025-41646
9.8An unauthorized remote attacker can bypass the authentication of the affected software package by misusing an incorrect type conversion. This leads to full compromise of the device
-
CVE-2025-5486
9.8The WP Email Debug plugin for WordPress is vulnerable to privilege escalation due to a missing capability check on the WPMDBUG_handle_settings() function in versions 1.0 to 1.1.0. This makes it...
-
CVE-2025-47966
9.8Exposure of sensitive information to an unauthorized actor in Power Automate allows an unauthorized attacker to elevate privileges over a network.
-
CVE-2025-5663 - SQL Injection vulnerability in PHPgurukul Auto/Taxi Stand Management System 1.0
9.8A vulnerability has been found in PHPGurukul Auto Taxi Stand Management System 1.0 and classified as critical. This vulnerability affects unknown code of the file /admin/search-autoortaxi.php. The...
-
CVE-2025-5701
9.8The HyperComments plugin for WordPress is vulnerable to unauthorized modification of data that can lead to privilege escalation due to a missing capability check on the hc_request_handler function...
-
CVE-2025-5639 - SQL Injection vulnerability in PHPgurukul Notice Board System 1.0
9.8A vulnerability was found in PHPGurukul Notice Board System 1.0 and classified as critical. Affected by this issue is some unknown functionality of the file /forgot-password.php. The manipulation...
-
CVE-2025-5629 - Classic Buffer Overflow vulnerability in Tenda Ac10 Firmware
9.8A vulnerability, which was classified as critical, was found in Tenda AC10 up to 15.03.06.47. This affects the function formSetPPTPServer of the file /goform/SetPptpServerCfg of the component HTTP...
-
CVE-2025-5625 - SQL Injection vulnerability in Campcodes Online Teacher Record Management System 1.0
9.8A vulnerability was found in Campcodes Online Teacher Record Management System 1.0. It has been rated as critical. This issue affects some unknown processing of the file /search-teacher.php. The...