Security News
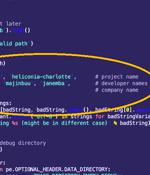
A Barcelona-based surveillanceware vendor named Variston IT is said to have surreptitiously planted spyware on targeted devices by exploiting several zero-day flaws in Google Chrome, Mozilla Firefox, and Windows, some of which date back to December 2018. "Their Heliconia framework exploits n-day vulnerabilities in Chrome, Firefox, and Microsoft Defender, and provides all the tools necessary to deploy a payload to a target device," Google Threat Analysis Group researchers Clement Lecigne and Benoit Sevens said in a write-up.
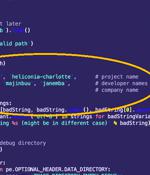
A Barcelona-based surveillanceware vendor named Variston IT is said to have surreptitiously planted spyware on targeted devices by exploiting several zero-day flaws in Google Chrome, Mozilla Firefox, and Windows, some of which date back to December 2018. "Their Heliconia framework exploits n-day vulnerabilities in Chrome, Firefox, and Microsoft Defender, and provides all the tools necessary to deploy a payload to a target device," Google Threat Analysis Group researchers Clement Lecigne and Benoit Sevens said in a write-up.

Zero-days are bugs for which there were zero days you could have updated proactively. Because cybercriminals not only found the bug first, but also figured out how to exploit it for nefarious purposes before a patch was prepared and published.

Google on Thursday released software updates to address yet another zero-day flaw in its Chrome web browser. Clement Lecigne of Google's Threat Analysis Group has been credited with reporting the flaw on November 22, 2022.

Google has released an emergency security update for the desktop version of the Chrome web browser, addressing the eighth zero-day vulnerability exploited in attacks this year.As users need time to apply the security update on their Chrome installations, Google has withheld details about the vulnerability to prevent expanding its malicious exploitation.

This Mark of the Web is an alternate data stream that contains information about the file, such as the URL security zone the file originates from, its referrer, and its download URL. When a user attempts to open a file with a MoTW attribute, Windows will display a security warning asking if they are sure they wish to open the file. After analyzing the files, Will Dormann, a senior vulnerability analyst at ANALYGENCE, discovered that the threat actors were using a new Windows zero-day vulnerability that prevented Mark of the Web security warnings from being displayed.

Photos: IRISSCON 2022IRISSCON, the annual cyber crime-themed conference organized by the Irish Reporting and Information Security Service, was held in Dublin, Ireland on Thursday, November 10, 2022. Security "Sampling" puts US federal agencies at riskTitania launched an independent research report that uncovers the impact of exploitable misconfigurations on the security of networks in the US federal government.

Windows has fixed a bug that prevented Mark of the Web flags from propagating to files within downloaded ISO files, dealing a massive blow to malware distributors and developers. According to Bill Demirkapi, an engineer in Microsoft MSRC's Vulnerability and Mitigations team, a bug was fixed that prevented the MoTW flag from propagating to files inside an ISO disk image.

Windows has fixed a bug that prevented Mark of the Web flags from propagating to files within downloaded ISO files, dealing a massive blow to malware distributors and developers. The MoTW flag is added to files as an alternate data stream called 'Zone.Identifier,' which includes what URL security zone the file is from, the referrer, and the URL to the file.

Microsoft's latest round of monthly security updates has been released with fixes for 68 vulnerabilities spanning its software portfolio, including patches for six actively exploited zero-days.Also separately addressed at the start of the month is an actively exploited flaw in Chromium-based browsers that was plugged by Google as part of an out-of-band update late last month.