Security News

Today, phishing is the fastest growing Internet crime, and a threat to both consumers and businesses. Finance, technology, and telecom brands were the most commonly impersonated industries, notably for the unprecedented access and financial benefit that bank accounts, email and social media, and phone companies can give attackers, according to Cloudflare.

What we didn't know, even as this case was grinding through the New York judicial system, was that SHEIN was adding some curious code to its Android app that turned it into a basic sort of "Marketing spyware tool". We then performed a dynamic analysis by running the app in an instrumented environment to observe the code, including how it read the clipboard and sent its contents to a remote server.

Well-known cybersecurity researcher Fabian Bräunlein has featured not once but twice before on Naked Security for his work in researching the pros and cons of Apple's AirTag products. Now, Bräunlein is back with another worthwhile warning, this time about the danger of cloud-based security lookup services that give you a free opinion about cybersecurity data you may have collected.
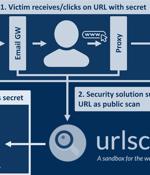
Security researchers are warning of "a trove of sensitive information" leaking through urlscan.io, a website scanner for suspicious and malicious URLs. "Sensitive URLs to shared documents, password reset pages, team invites, payment invoices and more are publicly listed and searchable," Positive Security co-founder, Fabian Bräunlein, said in a report published on November 2, 2022.

You may be familiar with some of the shortest internet domains used by major companies, such as m.me and fb. Although the vast majority of internet domains contain TLDs separated by one or more dots, turns out it's not a must for a domain.

Including Facebook, add parameters to the web address for tracking purposes. Mozilla introduced support for URL stripping in Firefox 102, which it launched in June 2022.
Mozilla Firefox 102 was released today with a new privacy feature that strips parameters from URLs that are used to track you around the web. Numerous companies, including Facebook, Marketo, Olytics, and HubSpot, utilize custom URL query parameters to track clicks on links.

Security researchers are seeing an uptick in the use of reverse tunnel services along with URL shorteners for large-scale phishing campaigns, making the malicious activity more difficult to stop. With reverse tunnels, threat actors can host the phishing pages locally on their own computers and route connections through the external service.

The Follina bug, now more properly known as CVE-2022-30190, hinges on a weird, non-standard URL supported by the Windows operating system. Windows includes a lengthy list of proprietary URL schemes, also known as protocol handlers, that can be used to trigger a range of non-standard activities simply by referencing the special URL. The Follina bug, for example, took devious advantage of the URL scheme ms-msdt:, which relates to system diagnostics.

Researchers uncover URL spoofing flaws on Zoom, Box, Google DocsResearchers have discovered several URL spoofing bugs in Box, Zoom and Google Docs that would allow phishers to generate links to malicious content and make it look like it's hosted by an organization's SaaS account. A 10-point plan to improve the security of open source softwareThe Linux Foundation and the Open Source Software Security Foundation, with input provided by executives from 37 companies and many U.S. government leaders, delivered a 10-point plan to broadly address open source and software supply chain security, by securing open source security production, improving vulnerability discovery and remediation, and shortening the patching response time of the ecosystem.