Security News
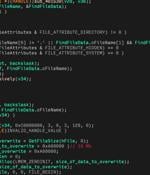
Two weeks after details emerged about a second data wiper strain delivered in attacks against Ukraine, yet another destructive malware has been detected amid Russia's continuing military invasion of the country. Slovak cybersecurity company ESET dubbed the third wiper "CaddyWiper," which it said it first observed on March 14 around 9:38 a.m. UTC. Metadata associated with the executable shows that the malware was compiled at 7:19 a.m. UTC, a little over two hours prior to its deployment.

Cybercriminals are targeting Ukrainian sympathizers, what can you do to remain safe? Cisco Talos published findings March 12 detailing a number of malware items being disguised as offensive cyber tools against Russian entities, when in actuality, the virus is designed to infect users who download the software.

Newly discovered data-destroying malware was observed earlier today in attacks targeting Ukrainian organizations and deleting data across systems on compromised networks. "This new malware erases user data and partition information from attached drives," ESET Research Labs explained.

A broad range of threat actors, including Fancy Bear, Ghostwriter, and Mustang Panda, have launched phishing campaigns against Ukraine, Poland, and other European entities amid Russia's invasion of Ukraine. Google's Threat Analysis Group said it took down two Blogspot domains that were used by the nation-state group FancyBear - which is attributed to Russia's GRU military intelligence - as a landing page for its social engineering attacks.

Yaroslav Vasinskyi, a Ukrainian national, linked to the Russia-based REvil ransomware group has been extradited to the U.S. to face charges for his role in carrying out the file-encrypting malware attacks against several companies, including Kaseya last July. The 22-year-old had been previously arrested in Poland in October 2021, prompting the U.S. Justice Department to file charges of conspiracy to commit fraud and related activity in connection with computers, damage to protected computers, and conspiracy to commit money laundering.

Ukraine's Computer Emergency Response Team warned of new phishing attacks aimed at its citizens by leveraging compromised email accounts belonging to three different Indian entities with the goal of compromising their inboxes and stealing sensitive information. "In this way, they gain access to the email inboxes of Ukrainian citizens."

MacPaw's ClearVPN enables secure connectivity, helps in supporting Ukrainian resistance. MacPaw's ClearVPN application not only assists in securely accessing content, enabling encrypted connections and securing online traffic and transactions, but with a recent update the VPN utility now also simplifies supporting Ukraine resistance efforts.

MacPaw's ClearVPN enables secure connectivity, helps in supping Ukrainian resistance. MacPaw's ClearVPN application not only assists in securely accessing content, enabling encrypted connections and securing online traffic and transactions, but with a recent update the VPN utility now also simplifies supporting Ukraine resistance efforts.

Internet security companies have recorded a massive wave of attacks against Ukrainian WordPress sites since Russia invaded Ukraine, aiming to take down the websites and cause general demoralization. Cybersecurity firm Wordfence, which protects 8,320 WordPress websites belonging to universities, government, military, and law enforcement entities in Ukraine, reports having recorded 144,000 attacks on February 25 alone.

Ukrainian news agency Ukrainska Pravda has claimed the nation's Centre for Defence Strategies think tank has obtained the online personal details of 120,000 Russian servicemen fighting in Ukraine. The Ukrainian news agency said the think tank obtained the personnel records from "Reliable sources." Whether or not the database is real, the impact on Russian military morale - knowing that your country's enemies have your personal details and can contact your family if you're captured, killed, or even still alive - won't be insignificant.