Security News

Lenovo has published a security advisory on vulnerabilities that impact its Unified Extensible Firmware Interface loaded on at least 100 of its laptop models. A total of three security issues were discovered, two of them allowing an attacker to disable the protection for the SPI flash memory chip where the UEFI firmware is stored and to turn off the UEFI Secure Boot feature, which ensures the system loads at boot time only code trusted by the Original Equipment Manufacturer.

Cybersecurity researchers on Tuesday disclosed 16 new high-severity vulnerabilities in various implementations of Unified Extensible Firmware Interface firmware impacting multiple HP enterprise devices. The shortcomings, which have CVSS scores ranging from 7.5 to 8.8, have been uncovered in HP's UEFI firmware.

HP has disclosed 16 high-impact UEFI firmware vulnerabilities that could allow threat actors to infect devices with malware that gain high privileges and remain undetectable by installed security software. SSM. CVE-2021-23924: heap buffer overflow leading to arbitrary code execution.

Researchers from firmware protection company Binarly have discovered critical vulnerabilities in the UEFI firmware from InsydeH2O used by multiple computer vendors such as Fujitsu, Intel, AMD, Lenovo, Dell, ASUS, HP, Siemens, Microsoft, and Acer. UEFI software is an interface between a device's firmware and the operating system, which handles the booting process, system diagnostics, and repair functions.

As many as 23 new high severity security vulnerabilities have been disclosed in different implementations of Unified Extensible Firmware Interface firmware used by numerous vendors, including Bull Atos, Fujitsu, HP, Juniper Networks, Lenovo, among others. The vulnerabilities reside in Insyde Software's InsydeH2O UEFI firmware, according to enterprise firmware security company Binarly, with a majority of the anomalies diagnosed in the System Management Mode.

A previously undocumented firmware implant deployed to maintain stealthy persistence as part of a targeted espionage campaign has been linked to the Chinese-speaking Winnti advanced persistent threat group. Kaspersky, which codenamed the rootkit MoonBounce, characterized the malware as the "Most advanced UEFI firmware implant discovered in the wild to date," adding "The purpose of the implant is to facilitate the deployment of user-mode malware that stages execution of further payloads downloaded from the internet."

Security analysts have discovered and linked MoonBounce, "The most advanced" UEFI firmware implant found in the wild so far, to the Chinese-speaking APT41 hacker group. Kaspersky couldn't retrieve that payload for analysis or figure out how exactly the actors infected the UEFI firmware in the first place.
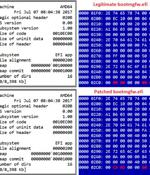
Cybersecurity researchers on Tuesday revealed details of a previously undocumented UEFI bootkit that has been put to use by threat actors to backdoor Windows systems as early as 2012 by modifying a legitimate Windows Boot Manager binary to achieve persistence, once again demonstrating how technology meant to secure the environment prior to loading the operating system is increasingly becoming a "Tempting target." Slovak cybersecurity firm ESET codenamed the new malware "ESPecter" for its ability to persist on the EFI System Partition, in addition to circumventing Microsoft Windows Driver Signature Enforcement to load its own unsigned driver that can be used to facilitate espionage activities such as document theft, keylogging, and screen monitoring by periodically capturing screenshots.

A newly discovered and previously undocumented UEFI bootkit has been used by attackers to backdoor Windows systems by hijacking the Windows Boot Manager since 2012. Bootkits are malicious code planted in the firmware invisible to security software that runs within the operating system since the malware is designed to load before everything else, in the initial stage of the booting sequence.
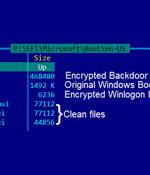
Commercially developed FinFisher surveillanceware has been upgraded to infect Windows devices using a UEFI bootkit using a trojanized Windows Boot Manager, marking a shift in infection vectors that allow it to elude discovery and analysis. While the tool was previously deployed through tampered installers of legitimate applications such as TeamViewer, VLC, and WinRAR that were backdoored with an obfuscated downloader, subsequent updates in 2014 enabled infections via Master Boot Record bootkits with the goal of injecting a malicious loader in a manner that's engineered to slip past security tools.