Security News

Researchers at the universities of California, Virginia, and Microsoft have devised a new poisoning attack that could trick AI-based coding assistants into suggesting dangerous code. Given the rise of coding assistants like GitHub's Copilot and OpenAI's ChatGPT, finding a covert way to stealthily plant malicious code in the training set of AI models could have widespread consequences, potentially leading to large-scale supply-chain attacks.
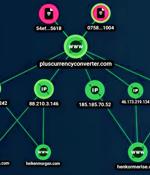
An Android banking trojan known as GodFather is being used to target users of more than 400 banking and cryptocurrency apps spanning across 16 countries. This includes 215 banks, 94 crypto wallet providers, and 110 crypto exchange platforms serving users in the U.S., Turkey, Spain, Italy, Canada, and Canada, among others, Singapore-headquartered Group-IB said in a report shared with The Hacker News.

The threat actors behind the Windows banking malware known as Casbaneiro has been attributed as behind a novel Android trojan called BrasDex that has been observed targeting Brazilian users as part of an ongoing multi-platform campaign. BrasDex features a "Complex keylogging system designed to abuse Accessibility Services to extract credentials specifically from a set of Brazilian targeted apps, as well as a highly capable Automated Transfer System engine," ThreatFabric said in a report published last week.
More than 300,000 users across 71 countries have been victimized by a new Android threat campaign called the Schoolyard Bully Trojan. Mainly designed to steal Facebook credentials, the malware is camouflaged as legitimate education-themed applications to lure unsuspecting users into downloading them.
More than 300,000 users across 71 countries have been victimized by a new Android threat campaign called the Schoolyard Bully Trojan. Mainly designed to steal Facebook credentials, the malware is camouflaged as legitimate education-themed applications to lure unsuspecting users into downloading them.

Google has removed two new malicious dropper apps that have been detected on the Play Store for Android, one of which posed as a lifestyle app and was caught distributing the Xenomorph banking malware. "Xenomorph is a trojan that steals credentials from banking applications on users' devices," Zscaler ThreatLabz researchers Himanshu Sharma and Viral Gandhi said in an analysis published Thursday.

As one of the oldest banking trojans - dating back to the mid-2000s - the software nasty has a number of variants and been given a few monikers, including URSNIF, Gozi, and ISFB. It's crossed paths with other malware families, had its source code leaked twice since 2016 and, according to Mandiant, is now less a single malware family than a "Set of related siblings." In a report this week, Mandiant researchers Sandor Nemes, Sulian Lebegue, and Jessa Valdez wrote that a strain of URSNIF's RM3 version is no longer a banking trojan but a generic backdoor, similar to the short-lived Saigon variant.

The notorious Android banking trojan known as SharkBot has once again made an appearance on the Google Play Store by masquerading as antivirus and cleaner apps. "This new dropper doesn't rely on Accessibility permissions to automatically perform the installation of the dropper Sharkbot malware," NCC Group's Fox-IT said in a report.
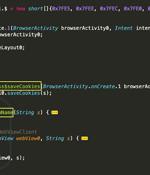
The SOVA Android banking trojan is continuing to be actively developed with upgraded capabilities to target no less than 200 mobile applications, including banking apps and crypto exchanges and wallets, up from 90 apps when it started out. In less than a year, the trojan has also acted as a foundation for another Android malware called MaliBot that's designed to target online banking and cryptocurrency wallet customers in Spain and Italy.
A previously unknown Android banking trojan has been discovered in the wild, targeting users of the Spanish financial services company BBVA. Said to be in its early stages of development, the malware - dubbed Revive by Italian cybersecurity firm Cleafy - was first observed on June 15, 2022 and distributed by means of phishing campaigns. "The name Revive has been chosen since one of the functionality of the malware is restarting in case the malware stops working, Cleafy researchers Federico Valentini and Francesco Iubatti said in a Monday write-up."