Security News

The USA and the United Kingdom have sanctioned eleven Russian nationals associated with the TrickBot and Conti ransomware cybercrime operations. After numerous takedown attempts by the U.S. government, the Conti ransomware gang took control of the TrickBot operation and its development, using it to enhance more advanced and stealthy malware, such as BazarBackdoor and Anchor.

"Current members of the TrickBot group are associated with Russian Intelligence Services," the U.S. Treasury Department noted. "The TrickBot group's preparations in 2020 aligned them to Russian state objectives and targeting previously conducted by Russian Intelligence Services."

The US and UK have sanctioned seven Russians for their alleged roles in disseminating Conti and Ryuk ransomware and the Trickbot banking trojan. Conti and Ryuk ransomware extorted at least £27 million from 149 UK individuals and businesses, according to the government's estimate.

The United States and the United Kingdom have sanctioned seven Russian individuals for their involvement in the TrickBot cybercrime group, whose malware was used to support attacks by the Conti and Ryuk ransomware operation. TrickBot is a cybercrime gang responsible for developing numerous malware families, such as the eponymous TrickBot malware, BazarBackdoor, Anchor, and BumbleBee.
In what's being described as an "Unprecedented" twist, the operators of the TrickBot malware have resorted to systematically targeting Ukraine since the onset of the war in late February 2022. "ITG23's campaigns against Ukraine are notable due to the extent to which this activity differs from historical precedent and the fact that these campaigns appeared specifically aimed at Ukraine with some payloads that suggest a higher degree of target selection," IBM Security X-Force analyst Ole Villadsen said in a technical report.

Orange Cyberdefense's CyberSOCs have been tracking the specific malware named Trickbot for quite some time. This threat analysis will be focused on the threat actor named TA551, and its use of Trickbot as an example.

"The C2 server serves as a botnet-as-a-service controlling nearly 230,000 vulnerable MikroTik routers," Avast's senior malware researcher, Martin Hron, said in a write-up, potentially linking it to what's now called the M?ris botnet. The botnet is known to exploit a known vulnerability in the Winbox component of MikroTik routers, enabling the attackers to gain unauthenticated, remote administrative access to any affected device.
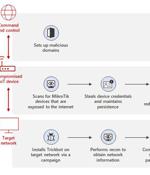
Microsoft on Wednesday detailed a previously undiscovered technique put to use by the TrickBot malware that involves using compromised Internet of Things devices as a go-between for establishing communications with the command-and-control servers. "By using MikroTik routers as proxy servers for its C2 servers and redirecting the traffic through non-standard ports, TrickBot adds another persistence layer that helps malicious IPs evade detection by standard security systems," Microsoft's Defender for IoT Research Team and Threat Intelligence Center said.

Cybersecurity firm Emsisoft has released a free decryption tool to help Diavol ransomware victims recover their files without paying a ransom. Diavol ransomware victims can download the free tool from Emsisoft's servers to decrypt their data using detailed instructions available in this usage guide [PDF].

Microsoft has published a tool that scans for and detects MikroTik-powered Internet-of-Things devices that have been hijacked by the Trickbot gang. The open-source scanner comes after an investigation by Redmond's Defender for IoT research team into how the nefarious malware crew takes over MikroTik routers and sets them up to funnel communications to and from Trickbot-infected computers on the network and the criminals' backend servers.