Security News

Threat actors are intensifying internet-wide scanning for Git configuration files that can reveal sensitive secrets and authentication tokens used to compromise cloud services and source code...

A proof-of-concept attack called "Cookie-Bite" uses a browser extension to steal browser session cookies from Azure Entra ID to bypass multi-factor authentication (MFA) protections and maintain...

Microsoft confirms that the weekend Entra account lockouts were caused by the invalidation of short-lived user refresh tokens that were mistakenly logged into internal systems. [...]

But this mystery isn't over yet, Unit 42 opines That massive GitHub supply chain attack that spilled secrets from countless projects? It traces back to a stolen token from a SpotBugs workflow -...

The cascading supply chain attack that initially targeted Coinbase before becoming more widespread to single out users of the "tj-actions/changed-files" GitHub Action has been traced further back...

A cascading supply chain attack on GitHub that targeted Coinbase in March has now been traced back to a single token stolen from a SpotBugs workflow, which allowed a threat actor to compromise...

Explore how relying on CSRF tokens as a security measure against CSRF attacks is a recommended best practice, but in some cases, they are simply not enough. Introduction As per the Open Web...
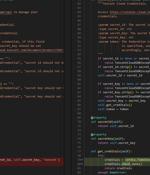
Cybersecurity researchers have warned of a malicious campaign targeting users of the Python Package Index (PyPI) repository with bogus libraries masquerading as "time" related utilities, but...

The immensely popular memecoin generator Pump.fun had its X account hacked to promote a fake "PUMP" token cryptocurrency scam. [...]

A malicious package named 'pycord-self' on the Python package index (PyPI) targets Discord developers to steal authentication tokens and plant a backdoor for remote control over the system. [...]