Security News

Scammers are estimated to have made $80 million per month by impersonating popular brands asking people to participate in fake surveys or giveaways. The scam themes are the typical and "Trustworthy" fake surveys and giveaways from popular brands with the holiday season making targets more susceptible to fraudulent gift offerings.
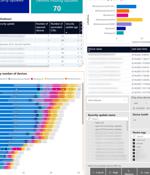
Want a custom security dashboard to bring together data from multiple places? Microsoft Power BI can do that and help you spot what's changing. Obviously, you can use Microsoft Power BI to monitor Power BI usage, using the Power BI Admin APIs to track who is accessing data and visualisations and make sure it's only the people you expect to have access to what might be critical or confidential business information.

In this interview with Help Net Security, Avi Bashan, CTO at Kovrr, talks about cyber insurance trends and how the growing threat landscape impacted both insurers and insurees. At the same time they feel more vulnerable to a ransomware attack than ever before, insurers are pulling back to the point where cyber insurance is more expensive than used to and thus demands clearer justification of the investment for most companies, and policies that cover a broad range of cyber incidents are more scarce.

The Log4j JNDI attack and how to prevent itThe disclosure of the critical Log4Shell vulnerability and the release of first one and than additional PoC exploits has been an unwelcome surprise for the entire information security community, but most of all those who are tasked with keeping enterprise systems and network secure. Ransomware hits HR solutions provider Kronos, locking customers out of vital servicesThe end of the year chaos caused by the revelation of the Log4Shell vulnerability has, for some organizations, been augmented by a ransomware attack on Ultimate Kronos Group, one of the biggest HR and workforce management solutions providers in the US. Microsoft patches spoofing vulnerability exploited by EmotetMicrosoft has delivered fixes for 67 vulnerabilities, including a spoofing vulnerability actively exploited to deliver Emotet/Trickbot/Bazaloader malware family.

The Cybersecurity and Infrastructure Security Agency warned critical infrastructure organizations today to strengthen their cybersecurity defenses against potential and ongoing threats. "In the lead up to the holidays and in light of persistent and ongoing cyber threats, CISA urges critical infrastructure owners and operators to take immediate steps to strengthen their computer network defenses against potential malicious cyber attacks," the cybersecurity agency said [PDF].

Others might have belonged to people who have changed roles and are no longer using those specific identities. These tools have blind spots in areas such as mismanaged empty groups and robotic identities.

With 2021 drawing to a close and many closing their plans and budgets for 2022, the time has come to do a brief wrap-up of the SaaS Security challenges on the horizon. Here are the top 3 SaaS security posture challenges as we see them.

The threat group, first identified in June, focuses solely on data exfiltration and subsequent extortion, and has already targeted 40 victims since September. There is a new financially motivated threat group on the rise and for a change, it doesn't appear to be interested in deploying ransomware or taking out high-profile targets.
![[eBook] Guide to Achieving 24x7 Threat Monitoring and Response for Lean IT Security Teams](/static/build/img/news/ebook-guide-to-achieving-24x7-threat-monitoring-and-response-for-lean-it-security-teams-small.jpg)
Teams can't afford to take a minute off, but they also can't manage the massive security necessary to defend most organizations. A new eBook by XDR provider Cynet breaks down this challenge and offers some solutions for lean security teams looking for ways to improve their detection and response capabilities.

The progress within modern application development doesn't directly translate to the security world as it often ends up being the aspect that gets left behind. Even worse, many of these vulnerabilities can go overlooked by security teams as they learn to navigate modern architectures that aren't immediately adaptable to their typical security testing practices.