Security News

Siloed approaches to securing human and machine identities are driving identity-based attacks across enterprises and their ecosystems, according to CyberArk. The CyberArk 2024 Identity Security Threat Landscape Report was conducted across private and public sector organizations of 500 employees and above. Machine identities often lack identity security controls.

Rockwell Automation is urging its customers to disconnect all industrial control systems (ICSs) not meant to be connected to the public-facing internet to mitigate unauthorized or malicious cyber...

Cisco’s Splunk Acquisition Should Help Security Pros See Threats Sooner in Australia and New Zealand
Craig Bates, Splunk vice president of Australia and New Zealand, said the deal will help customers defend against modern threats by tooling security operations centres up with end-to-end security and observability. He added security data unification will be key to organisations in the future as they battle threats increasingly launched with the aid of AI. What does the Cisco and Splunk combination mean for cyber security software customers?

The Federal Communications Commission has named its first officially designated robocall threat actor 'Royal Tiger,' a move aiming to help international partners and law enforcement more easily track individuals and entities behind repeat robocall campaigns. The Royal Tiger group, allegedly led by Prince Jashvantlal Anand and his associate Kaushal Bhavsar, is operating multiple entities linked to illegal calls in the United States, including VoIP companies Illum Telecommunication Limited, PZ Telecommunication LLC, and One Eye LLC. They routed robocalls in the United States to Texas-based Great Choice Telecom, previously the target of a $225 million forfeiture order and cease-and-desist letters from the FCC and the FTC for placing illegal spoofed robocalls.
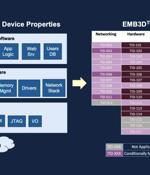
The MITRE Corporation has officially made available a new threat-modeling framework called EMB3D for makers of embedded devices used in critical infrastructure environments. "The model provides a...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Artificial intelligence (AI) is transforming cybersecurity, and those leading the charge are using it to outsmart increasingly advanced cyber threats. Join us for an exciting webinar, "The Future...

The thunderstorms of April patches have passed, and it has been pretty calm leading up to May 2024 Patch Tuesday. April 2024 Patch Tuesday turned out to be a busy one with 150 new CVEs addressed by Microsoft.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

In this Help Net Security video, Gabi Reish, Chief Business Development and Product Officer at Cybersixgill, discusses the role of threat intelligence in every enterprise's security stack. Threat intelligence plays a significant role in proactively managing a company's threat exposure.