Security News
A new remote access trojan called QwixxRAT is being advertised for sale by its threat actor through Telegram and Discord platforms. "Once installed on the victim's Windows platform machines, the RAT stealthily collects sensitive data, which is then sent to the attacker's Telegram bot, providing them with unauthorized access to the victim's sensitive information," Uptycs said in a new report published today.

Asian smartphone giant Xiaomi is now blocking Telegram from being installed on devices using its MIUI system and firmware interface. If an app is deemed malicious or dangerous, MIUI tries to remove the app from the device and block the installation.

As a result, many of these illicit Telegram networks have negatively impacted many industries in relation to the increase of cyberattacks and data leaks that have occurred across the globe. While any industry can be affected by the cybercriminals operating on Telegram, there are several industries that are more significantly impacted by these illicit activities.

In this post, we're going to explore common threat actors and their activities on dark web forums versus illicit Telegram communities. Hackers on dark web forums are more commonly known to share more zero-day exploits to other threat actors as well as share with other hackers how to use these exploits to their advantage as well.

Threat actors, ransomware gangs, malware developers, and others are increasingly and rapidly moving off of the "Traditional" dark web and onto illicit Telegram channels specializing in cybercrime. Level of technical proficiency to find cybercrime channels and successfully make purchases is even lower than Tor, creating a democratization of cybercrime data.
India's tech minister Rajeev Chandrasekhar confirmed "A Telegram Bot was throwing up Co-WIN app details upon entry of phone numbers," but claimed the data came from a previous breach unrelated to Co-WIN. India's Ministry of Health and Family Welfare later denied any breach, writing "It is clarified that all such reports are without any basis and mischievous in nature." "Union Health Ministry has requested the Indian Computer Emergency Response Team to look into this issue and submit a report. In addition, an internal exercise has been initiated to review the existing security measures of Co-WIN," states a Ministerial announcement.

The malware peddlers' focus on Apple fans was clearly reflected in the name they gave their "Product": Atomic macOS Stealer, or AMOS for short. Well-informed Mac users should spot that the popup produced clearly belongs to the malware app itself, which is imaginatively called Setup.

A novel credential-stealing malware called Zaraza bot is being offered for sale on Telegram while also using the popular messaging service as a command-and-control. "Zaraza bot targets a large number of web browsers and is being actively distributed on a Russian Telegram hacker channel popular with threat actors," cybersecurity company Uptycs said in a report published last week.
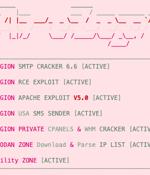
An emerging Python-based credential harvester and a hacking tool named Legion is being marketed via Telegram as a way for threat actors to break into various online services for further exploitation. The malware is suspected to be linked to another malware family called AndroxGh0st that was first documented by cloud security services providerLacework in December 2022.
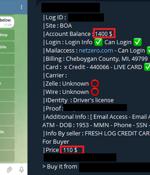
In yet another sign that Telegram is increasingly becoming a thriving hub for cybercrime, researchers have found that threat actors are using the messaging platform to peddle phishing kits and help set up phishing campaigns. "To promote their 'goods,' phishers create Telegram channels through which they educate their audience about phishing and entertain subscribers with polls like, 'What type of personal data do you prefer?'," Kaspersky web content analyst Olga Svistunova said in a report published this week.