Security News

An app with the name Signal Plus Messenger was available on Play for nine months and had been downloaded from Play roughly 100 times before Google took it down last April after being tipped off by security firm ESET. It was also available in the Samsung app store and on signalplus[. An app calling itself FlyGram was created by the same threat actor and was available through the same three channels.

At the time the researchers published their report, several malicious apps were still available for download through Google Play. The Telegram apps presented in Kaspersky's report are promoted as "Faster" alternatives to the regular app.
Spyware masquerading as modified versions of Telegram have been spotted in the Google Play Store that's designed to harvest sensitive information from compromised Android devices. The apps have been collectively downloaded millions of times before they were taken down by Google.

ESET researchers have identified two active campaigns targeting Android users, where the threat actors behind the tools for Telegram and Signal are attributed to the China-aligned APT group GREF. Most likely active since July 2020 and since July 2022, respectively for each malicious app, the campaigns have distributed the Android BadBazaar espionage code through the Google Play store, Samsung Galaxy Store, and dedicated websites posing as legitimate encrypted chat applications - the malicious apps are FlyGram and Signal Plus Messenger. Threat actors exploit fake Signal and Telegram apps.

Trojanized Signal and Telegram apps containing the BadBazaar spyware were uploaded onto Google Play and Samsung Galaxy Store by a Chinese APT hacking group known as GREF. [...]
Cybersecurity researchers have discovered malicious Android apps for Signal and Telegram distributed via the Google Play Store and Samsung Galaxy Store that are engineered to deliver the BadBazaar spyware on infected devices. Slovakian company ESET attributed the campaign to a China-linked actor called GREF. "Most likely active since July 2020 and since July 2022, respectively, the campaigns have distributed the Android BadBazaar espionage code through the Google Play store, Samsung Galaxy Store, and dedicated websites representing the malicious apps Signal Plus Messenger and FlyGram," security researcher Lukáš Štefanko said in a new report shared with The Hacker News.
In yet another sign that developers continue to be targets of software supply chain attacks, a number of malicious packages have been discovered on the Rust programming language's crate registry. It's not clear what the end goal of the campaign was, but the suspicious modules were found to harbor functionalities to capture the operating system information and transmit the data to a hard-coded Telegram channel via the messaging platform's API. This suggests that the campaign may have been in its early stages and that the threat actor may have been casting a wide net to compromise as many developer machines as possible to deliver rogue updates with improved data exfiltration capabilities.
Dubbed Telekopye, a portmanteau of Telegram and kopye, the toolkit functions as an automated means to create a phishing web page from a premade template and send the URL to potential victims, codenamed Mammoths by the criminals. The attack chains proceed thus: Neanderthals find their Mammoths and try to build rapport with them, before sending a bogus link created using the Telekopye phishing kit via email, SMS, or a direct message.
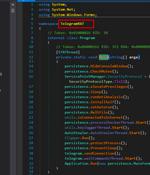
A new remote access trojan called QwixxRAT is being advertised for sale by its threat actor through Telegram and Discord platforms. "Once installed on the victim's Windows platform machines, the RAT stealthily collects sensitive data, which is then sent to the attacker's Telegram bot, providing them with unauthorized access to the victim's sensitive information," Uptycs said in a new report published today.

Asian smartphone giant Xiaomi is now blocking Telegram from being installed on devices using its MIUI system and firmware interface. If an app is deemed malicious or dangerous, MIUI tries to remove the app from the device and block the installation.