Security News

In this Help Net Security interview, Okey Obudulu, CISO at Skillsoft, talks about the increasing complexity of the CISO role and challenges they face. With the increasing complexity of the CISO role, what are the top three challenges you believe they face, and how can they best address these?

How To Use This Report Enhance situational awareness of techniques used by threat actors Identify potential attacks targeting your industry Gain insights to help improve and accelerate your...

India is grappling with a three-and-a-half year surge in cyber crime, with analysis suggesting cities like Bengaluru and Gurgaon - centers of India's tech development - are also hubs of evil activity. The report - A Deep Dive into Cybercrime Trends Impacting India from the non-profit Future Crime Research Foundation - identified cyber crime hot spots, as well as the most popular types of infosec assaults, from January 2020 until June 2023.

64% of IT leaders believe that cybersecurity concerns are negatively impacting their organization's willingness to invest in innovative tech, according to a report by HPE Aruba Networking. There is also a growing gulf between tech demands and the IT team's capability to manage it all - 66% of IT leaders have concerns about their organization's ability to keep up with the latest tech and digital demands, and 55% say their IT teams are already stretched to capacity.

The power of the EU's Digital Services Act to actually police the world's very large online platforms has been tested in a new study focused on Russian social media disinformation. The independent study of the DSA's risk management framework published by the EU's executive arm, the European Commission, concluded that commitments by social media platforms to mitigate the reach and influence of global online disinformation campaigns have been generally unsuccessful.
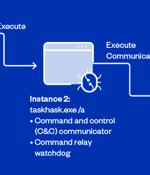
A hacking outfit nicknamed Earth Estries has been attributed to a new, ongoing cyber espionage campaign targeting government and technology industries based in the Philippines, Taiwan, Malaysia, South Africa, Germany, and the U.S. "The threat actors behind Earth Estries are working with high-level resources and functioning with sophisticated skills and experience in cyber espionage and illicit activities," Trend Micro researchers Ted Lee, Lenart Bermejo, Hara Hiroaki, Leon M Chang, and Gilbert Sison said. Active since at least 2020, Earth Estries is said to share tactical overlaps with another nation-state group tracked as FamousSparrow, which was first exposed by ESET in 2021 as exploiting ProxyLogon flaws in Microsoft Exchange Server to penetrate hospitality, government, engineering, and legal sectors.

Two U.K. teenagers have been convicted by a jury in London for being part of the notorious LAPSUS$ transnational gang and for orchestrating a series of brazen, high-profile hacks against major tech firms and demanding a ransom in exchange for not leaking the stolen information. Central to pulling off the extortion schemes was their ability to conduct SIM swapping and prompt bombing attacks to gain unauthorized access to corporate networks after an extensive social engineering phase.
Cybersecurity researchers have detailed an updated version of an advanced fingerprinting and redirection toolkit called WoofLocker that's engineered to conduct tech support scams. The sophisticated traffic redirection scheme was first documented by Malwarebytes in January 2020, leveraging JavaScript embedded in compromised websites to perform anti-bot and web traffic filtering checks to serve next-stage JavaScript that redirects users to a browser locker.

The former chief executive of a company that was sold to Qualcomm for more than $150 million has pleaded guilty to one count of money laundering relating to a $1.5 million transaction involving proceeds from the deal. Sanjiv Taneja was CEO at startup Abreezio, for which Qualcomm agreed to pay roughly $180 million, $150 million of which was paid in cash in October 2015.

Evidence from Oxford University's Fairwork Project cited in the report also notes that the UK GDPR provides a "Certain degree of protection for private individuals. However, it is more limited in protecting workers in the workplace." OII researcher Dr Matthew Cole noted in his evidence that: "Unless there is a union that is litigating around these things or an existing collective bargaining agreement, there is a lack of enforcement at the state level. The UK government could do much better at ensuring protections for worker data and protecting citizens of the UK from global giants like Uber, for example."