Security News

In the high-stakes world of cybersecurity, the battleground has shifted. Supply chain attacks have emerged as a potent threat, exploiting the intricate web of interconnected systems and...

Protobom is an open-source software supply chain tool that enables all organizations, including system administrators and software development communities, to read and generate Software Bill of Materials, file data, and translate this data across standard industry SBOM formats. The key to strengthening software security and software supply chain risk management is an SBOM, which is a nested, formatted inventory that lists the software's components, including the supply chain relationships of various open-source and commercial components used in building software.

A threat actor quietly spent the last two years integrating themself in the core team of maintainers of XZ Utils, a free software command-line data compressor widely used in Linux systems. The CVE-2024-3094 backdoor found in XZ Utils was implemented to interfere with authentication in SSHD, the OpenSSH server software that handles SSH connections.
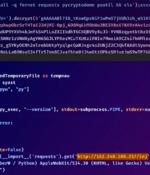
Unidentified adversaries orchestrated a sophisticated attack campaign that has impacted several individual developers as well as the GitHub organization account associated with Top.gg, a Discord...

The China-linked threat actor known as Evasive Panda orchestrated both watering hole and supply chain attacks targeting Tibetan users at least since September 2023. The end of the attacks is to...

NIST released its final guidelines for integrating software supply chain security in DevSecOps CI/CD pipelines. In this Help Net Security video, Henrik Plate, Security Researcher at Endor Labs, talks about this report, which provides actionable measures to integrate the various building blocks of software supply chain security assurance into CI/CD pipelines to enhance the preparedness of organizations to address supply chain security in the development and deployment of cloud-native applications.

Cybersecurity researchers have found that it's possible to compromise the Hugging Face Safetensors conversion service to ultimately hijack the models submitted by users and result in supply chain...

In an advisory today Germany's federal intelligence agency and South Korea's National Intelligence Service warn of an ongoing cyber-espionage operation targeting the global defense sector on behalf of the North Korean government. Today's joint cybersecurity advisory highlights two cases attributed to North Korean actors, one of them the Lazarus group, to provide the tactics, techniques, and procedures used by the attackers.

In this Help Net Security interview, Nate Warfield, Director of Threat Research and Intelligence at Eclypsium, outlines the crucial tasks for CISOs in protecting supply chains and achieving comprehensive visibility. Auditing a hardware supply chain is exponentially more difficult, as vendors may or may not choose to disclose what their underlying operating systems are, what open source software they use, where they source the hardware components of their devices, what firmware runs both the device itself and its subcomponents - for example a router may run a Linux distribution, with an open source routing daemon, a motherboard from Supermicro, with high-speed NICs from Mellanox, a baseboard management controller from ASPEED with BMC code from AMI which itself is another version of Linux with its own SBOM. With the apparent disconnect between security and development teams in software supply chain security, what strategies do you recommend to enhance collaboration?

In a world where more & more organizations are adopting open-source components as foundational blocks in their application's infrastructure, it's difficult to consider traditional SCAs as complete...