Security News

A malicious package in the Node Package Manager index uses invisible Unicode characters to hide malicious code and Google Calendar links to host the URL for the command-and-control location. [...]

Cybersecurity researchers have discovered a malicious package named "os-info-checker-es6" that disguises itself as an operating system information utility to stealthily drop a next-stage payload...

Inside the most innocent-looking image, a breathtaking landscape, or a funny meme, something dangerous could be hiding, waiting for its moment to strike. No strange file names. No antivirus...

A new campaign conducted by the TA558 hacking group is concealing malicious code inside images using steganography to deliver various malware tools onto targeted systems. The researchers identified over 320 attacks in this campaign that affected various sectors and countries.

A hacking group tracked as 'UAC-0184' was observed utilizing steganographic image files to deliver the Remcos remote access trojan onto the systems of a Ukrainian entity operating in Finland. Steganography is a well-documented but rarely seen tactic that involves encoding malicious code into the pixel data of images to evade detection by solutions using signature-based rules.
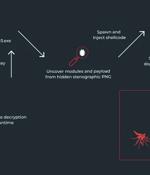
Ukrainian entities based in Finland have been targeted as part of a malicious campaign distributing a commercial remote access trojan known as Remcos RAT using a malware loader called IDAT Loader....

Phishing attacks are steadily becoming more sophisticated, with cybercriminals investing in new ways of deceiving victims into revealing sensitive information or installing malicious software. One...

Abstract: Steganography is the practice of encoding secret information into innocuous content in such a manner that an adversarial third party would not realize that there is hidden meaning. While this problem has classically been studied in security literature, recent advances in generative models have led to a shared interest among security and machine learning researchers in developing scalable steganography techniques.

From an article about Zheng Xiaoqing, an American convicted of spying for China: According to a Department of Justice (DOJ) indictment, the US citizen hid confidential files stolen from his...

A threat group tracked as 'Worok' hides malware within PNG images to infect victims' machines with information-stealing malware without raising alarms. Avast's report is based on additional artifacts the company captured from Worok attacks, confirming ESET's assumptions about the nature of the PNG files and adding new information on the type of malware payloads and the data exfiltration method.