Security News
A previously undocumented China-aligned threat actor has been linked to a set of adversary-in-the-middle (AitM) attacks that hijack update requests from legitimate software to deliver a...

A US court has rejected spyware vendor NSO Group's motion to dismiss a lawsuit filed by Apple that alleges the developer violated computer fraud and other laws by infecting customers' iDevices with its surveillance software. Apple sued NSO, developer of the notorious Pegasus spyware, back in November 2021 and asked the court to permanently ban NSO from using any Apple software, services, or devices.

Security researchers found that infections with high-profile spyware Pegasus, Reign, and Predator could be discovered on compromised Apple mobile devices by checking Shutdown. Kaspersky released Python scripts to help automate the process of analyzing the Shutdown.

Kaspersky's researchers have developed a lightweight method to detect indicators of infection from sophisticated iOS spyware such as NSO Group's Pegasus, QuaDream's Reign, and Intellexa's Predator through analyzing a log file created on iOS devices. "The sysdiag dump analysis proves to be minimally intrusive and resource-light, relying on system-based artifacts to identify potential iPhone infections. Having received the infection indicator in this log and confirmed the infection using Mobile Verification Toolkit processing of other iOS artifacts, this log now becomes part of a holistic approach to investigating iOS malware infection," said Maher Yamout, Lead Security Researcher at Kaspersky's Global Research and Analysis Team.

Cybersecurity researchers have identified a "lightweight method" called iShutdown for reliably identifying signs of spyware on Apple iOS devices, including notorious threats like NSO...

The Known Exploited Vulnerabilities catalog, or KEV for short, contains security issues that have been actively exploited in the wild. CISA has given federal agencies until January 29 to patch the six actively exploited flaws or stop using the vulnerable products.

Cybersecurity company ESET released its H2 2023 threat report, and we're highlighting three particularly interesting topics in it: the abuse of the ChatGPT name by cybercriminals, the rise of the Lumma Stealer malware and the Android SpinOk SDK spyware. In the second half of 2023, ESET has blocked 650,000 attempts to access malicious domains whose names include "Chatgpt" or similar string in an apparent reference to the ChatGPT chatbot.

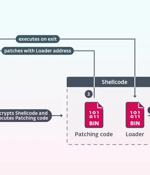
A new analysis of the sophisticated commercial spyware called Predator has revealed that its ability to persist between reboots is offered as an "add-on feature" and that it depends on the...

Urdu-speaking readers of a regional news website that caters to the Gilgit-Baltistan region have likely emerged as a target of a watering hole attack designed to deliver a previously undocumented Android spyware dubbed Kamran. The campaign, ESET has discovered, leverages Hunza News, which, when opened on a mobile device, prompts visitors of the Urdu version to install its Android app directly hosted on the website.

Cybersecurity researchers have unearthed a number of WhatsApp mods for Android that come fitted with a spyware module dubbed CanesSpy. These modified versions of the instant messaging app have...