Security News
How each side collects the adversary's smartphone location data and shields their own can mean the difference between victory and defeat. Because mobile app location data is often sold to commercial data brokers and then repackaged and sold to individual customers, a country can access such a database and then pick out the phones likely belonging to soldiers.

Kaspersky has launched a new information hub to help with their open-source stalkerware detection tool named TinyCheck, created in 2019 to help people detect if their devices are being monitored. Since TinyCheck doesn't need to run on the device itself, it can identify stalkerware presence on any mobile OS, including Android and iOS. TinyCheck will only look at the signs of abuse, like which servers receive communication from the device and won't read the contents of the victim's communications, like SMSs and emails.

A week after it emerged that sophisticated mobile spyware dubbed Hermit was used by the government of Kazakhstan within its borders, Google said it has notified Android users of infected devices. Necessary changes have been implemented in Google Play Protect - Android's built-in malware defense service - to protect all users, Benoit Sevens and Clement Lecigne of Google Threat Analysis Group said in a Thursday report.

Researchers warn Bluetooth signals can be used to track device owners via a unique fingerprinting of the radio signal. The paper suggests that minor manufacturing imperfections in hardware are unique with each device, and cause measurable distortions which can be used as a "Fingerprint to track a specific device".
Researchers at the University of Hamburg in Germany have conducted a field experiment capturing hundreds of thousands of passersby's WiFi connection probe requests to determine the type of data transmitted without the device owners realizing it. WiFi probing is a standard process, part of the bilateral communication required between a smartphone and an access point to establish a connection.
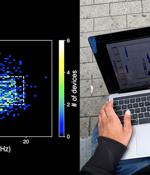
A new research undertaken by a group of academics from the University of California San Diego has revealed for the first time that Bluetooth signals can be fingerprinted to track smartphones. "To perform a physical-layer fingerprinting attack, the attacker must be equipped with a Software Defined Radio sniffer: a radio receiver capable of recording raw IQ radio signals," the researchers said in a new paper titled "Evaluating Physical-Layer BLE Location Tracking Attacks on Mobile Devices."

The principle of distinction between the two roles is a critical cornerstone of international humanitarian law-the law of armed conflict, codified by decades of customs and laws such as the Geneva Conventions. Those considered civilians and civilian targets are not to be attacked by military forces; as they are not combatants, they should be spared.

A critical security flaw has been uncovered in UNISOC's smartphone chipset that could be potentially weaponized to disrupt a smartphone's radio communications through a malformed packet. "Left unpatched, a hacker or a military unit can leverage such a vulnerability to neutralize communications in a specific location," Israeli cybersecurity company Check Point said in a report shared with The Hacker News.

Critical flaw found inside the UNISOC smartphone chip. Check Point Research has identified what it is calling a critical security vulnerability in UNISOC's smartphone chip, which is responsible for cellular communication in 11% of the world's smartphones.

A Bluetooth Low Energy vulnerability discovered by NCC Group researchers may be used by attackers to unlock Teslas, residential smart locks, building access systems, mobile phones, laptops, and many other devices. "Many products implement Bluetooth Low Energy-based proximity authentication, where the product unlocks or remains unlocked when a trusted BLE device is determined to be nearby," they explained, and added that the possibility of relay attacks against BLE proximity authentication has been known for years, but existing tools came with detectable levels of latency and were not capable of relaying connections employing link layer encryption.