Security News

A serious security vulnerability in a popular product from Apache has opened the floodgates for cybercriminals to try to attack susceptible servers. Hackers know that organizations are often slow to patch even critical security flaws, which is why attackers are frantically hunting for unpatched systems.

The bug, now officially denoted CVE-2021-44248, involves sending a request to a vulnerable server in which you include some data - for example, an HTTP header - that you expect the server will write to its logfile. Not just any old download: if the data that comes back is a valid Java program, then the server runs that file to "Help" it generate the logging data.

Need to lock down that Linux server so certain remote users can only access a specific directory and only for file upload and download purposes? Jack Wallen shows you how. When you have a server with SSH access, unless you've configured it otherwise, any user with an account on that system can log in and, if they have the permissions and skill, wreak havoc on your server.

At least 17 malware-laced packages have been discovered on the NPM package Registry, adding to a recent barrage of malicious software hosted and delivered through open-source software repositories such as PyPi and RubyGems. DevOps firm JFrog said the libraries, now taken down, were designed to grab Discord access tokens and environment variables from users' computers as well as gain full control over a victim's system.

A series of malicious packages in the Node.js package manager code repository are looking to harvest Discord tokens, which can be used to take over unsuspecting users' accounts and servers. Js, which enables interaction with the Discord API. "The malware's author took the original discord.js library as the base and injected obfuscated malicious code into the file src/client/actions/UserGet.js," according to JFrog, which added, "In classic trojan manner, the packages attempt to misdirect the victim by copying the README.md from the original package."

Microsoft says the first Secured-core certified Windows Server and Microsoft Azure Stack HCI devices are now available to protect customers' networks from security threats, including ransomware attacks. The newly certified Secured-core servers use Secure boot and the Trusted Platform Module 2.0 to ensure that only trusted will be able to load on boot.

NASA has upgraded its near-Earth asteroid monitoring algorithm to model hazardous space rocks more accurately after nearly two decades, it announced on Tuesday. Astronomers working at the space agency's Center for Near Earth Object Studies can now automatically calculate thermal influences that nudge an asteroid's orbit, potentially sending it hurtling towards our home planet.

Cerber ransomware is back, as a new ransomware family adopts the old name and targets Atlassian Confluence and GitLab servers using remote code execution vulnerabilities. As ransomware began picking up pace in 2016, a new Cerber ransomware operation emerged that quickly became one of the most prolific gangs at the time.
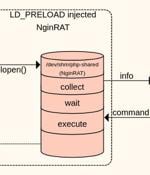
E-commerce platforms in the U.S., Germany, and France have come under attack from a new form of malware that targets Nginx servers in an attempt to masquerade its presence and slip past detection by security solutions. "This novel code injects itself into a host Nginx application and is nearly invisible," Sansec Threat Research team said in a new report.

eCommerce servers are being targeted with remote access malware that hides on Nginx servers in a way that makes it virtually invisible to security solutions. NginRAT was found on eCommerce servers in North America and Europe that had been infected with CronRAT, a remote access trojan that hides payloads in tasks scheduled to execute on an invalid day of the calendar.