Security News

The backdoor malware is deployed in a custom and malicious firmware designed specifically for TP-Link routers so that the hackers can launch attacks appearing to originate from residential networks. While Check Point has not determined how the attackers infect TP-Link routers with the malicious firmware image, they said it could be by exploiting a vulnerability or brute-forcing the administrator's credentials.
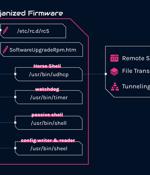
The Chinese nation-state actor known as Mustang Panda has been linked to a new set of sophisticated and targeted attacks aimed at European foreign affairs entities since January 2023. An analysis of these intrusions, per Check Point researchers Itay Cohen and Radoslaw Madej, has revealed a custom firmware implant designed explicitly for TP-Link routers.
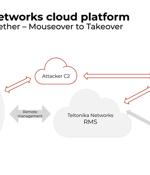
Several security vulnerabilities have been disclosed in cloud management platforms associated with three industrial cellular router vendors that could expose operational technology networks to external attacks. The 11 vulnerabilities allow "Remote code execution and full control over hundreds of thousands of devices and OT networks - in some cases, even those not actively configured to use the cloud."
As many as five security flaws have been disclosed in Netgear RAX30 routers that could be chained to bypass authentication and achieve remote code execution. "Successful exploits could allow attackers to monitor users' internet activity, hijack internet connections, and redirect traffic to malicious websites or inject malware into network traffic," Claroty security researcher Uri Katz said in a report.

The US government's Cybersecurity and Infrastructure Security Agency is adding three more flaws to its list of known-exploited vulnerabilities, including one involving TP-Link routers that is being targeted by the operators of the notorious Mirai botnet. Trend Micro's Zero Day Initiative threat-hunting group early last week wrote in a report that in mid-April miscreants behind the please-can't-it-just-die Mirai botnet were beginning to exploit the flaw primarily by attacking devices in Eastern Europe, though the campaign soon expanded beyond that region.

Threat actor APT28 is exploiting an old vulnerability in Cisco routers using Simple Network Management Protocol versions 1, 2c and 3 to target the U.S., Europe and Ukraine. The advisory states that in 2021, APT28 used malware to exploit an SNMP vulnerability, known as CVE-2017-6742, that was reported and patched on June 29, 2017, by Cisco.

The Mirai malware botnet is actively exploiting a TP-Link Archer A21 WiFi router vulnerability tracked as CVE-2023-1389 to incorporate devices into DDoS swarms. Researchers first abused the flaw during the Pwn2Own Toronto hacking event in December 2022, where two separate hacking teams breached the device using different pathways.

Enterprise-level network equipment on the secondary market hide sensitive data that hackers could use to breach corporate environments or to obtain customer information. Core routers are the backbone of a large network as they connect all other network devices.

U.K. and U.S. cybersecurity and intelligence agencies have warned of Russian nation-state actors exploiting now-patched flaws in networking equipment from Cisco to conduct reconnaissance and deploy malware against targets. The activity has been attributed to a threat actor tracked as APT28, which is also known as Fancy Bear, Forest Blizzard, FROZENLAKE, and Sofacy, and is affiliated with the Russian General Staff Main Intelligence Directorate.

"We would expect medium-sized to enterprise companies to have a strict set of security initiatives to decommission devices, but we found the opposite. Organizations need to be much more aware of what remains on the devices they put out to pasture, since a majority of the devices we obtained from the secondary market contained a digital blueprint of the company involved, including, but not limited to, core networking information, application data, corporate credentials, and information about partners, vendors, and customers," Camp continued. Organizations often recycle aging tech through third-party companies that are charged with verifying the secure destruction or recycling of digital equipment and the disposal of the data contained therein.