Security News
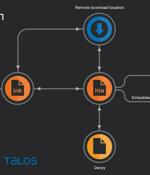
A relatively new threat actor known as YoroTrooper is likely made of operators originating from Kazakhstan. The assessment, which comes from Cisco Talos, is based on their fluency in Kazakh and...

WithSecure researchers have tracked attacks using DarkGate malware to an active cluster of cybercriminals operating out of Vietnam. DarkGate is a remote access trojan that has been used in attacks since at least 2018 and is currently available to cybercriminals as Malware-as-a-Service.

ClearFake, a recently documented threat leveraging compromised WordPress sites to push malicious fake browser updates, is likely operated by the threat group behind the SocGholish "Malware delivery via fake browser updates" campaigns, Sekoia researchers have concluded. Subsequently downloaded payloads create an iframe element to host the fake update interface, download that interface, and the fake update content and HTML page.

The advanced persistent threat (APT) actor known as ToddyCat has been linked to a new set of malicious tools that are designed for data exfiltration, offering a deeper insight into the hacking...
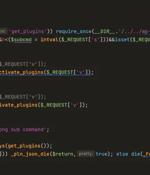
Cybersecurity researchers have shed light on a new sophisticated strain of malware that masquerades a WordPress plugin to stealthily create administrator accounts and remotely control a...
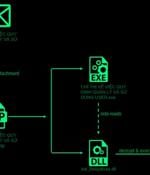
High-profile government and telecom entities in Asia have been targeted as part of an ongoing campaign since 2021 that's designed to deploy basic backdoors and loaders for delivering next-stage...

Cue files - which store the metadata that defines the layout of music on a CD. Given that it's often used alongside the FLAC audio format, open source audio players like Audacious are dependent on the library. The tracker-miners application initializes automatically when a file is either added or modified in a subdirectory of the home directory.

A previously undocumented threat actor of unknown provenance has been linked to a number of attacks targeting organizations in the manufacturing, IT, and biomedical sectors in Taiwan. The Symantec...

About 100,000 industrial control systems were found on the public web, exposed to attackers probing them for vulnerabilities and at risk of unauthorized access. Among them are power grids, traffic light systems, security and water systems.

New findings have identified connections between an Android spyware called DragonEgg and another sophisticated modular iOS surveillanceware tool named LightSpy. DragonEgg, alongside WyrmSpy (aka...