Security News

The Clop ransomware gang has been looking for ways to exploit a now-patched zero-day in the MOVEit Transfer managed file transfer solution since 2021, according to Kroll security experts. "Kroll observed activity consistent with MOVEit Transfer exploitation that collectively occurred on April 27, 2022; May 15-16, 2023; and May 22, 2023, indicating that actors were testing access to organizations via likely automated means and pulling back information from the MOVEit Transfer servers to identify which organization they were accessing," the report reveals.

The Clop ransomware gang has been looking for ways to exploit a now-patched zero-day in the MOVEit Transfer managed file transfer solution since 2021, according to Kroll security experts. "Kroll observed activity consistent with MOVEit Transfer exploitation that collectively occurred on April 27, 2022; May 15-16, 2023; and May 22, 2023, indicating that actors were testing access to organizations via likely automated means and pulling back information from the MOVEit Transfer servers to identify which organization they were accessing," the report reveals.

Pharmaceutical company Eisai has disclosed it suffered a ransomware incident that impacted its operations, admitting that attackers encrypted some of its servers. Eisai is a Tokyo-based pharmaceutical company with an annual revenue of $5.3 billion and over 10,000 employees.

The U.S. Cybersecurity and Infrastructure Security Agency and Federal Bureau of Investigation have published a joint advisory regarding the active exploitation of a recently disclosed critical flaw in Progress Software's MOVEit Transfer application to drop ransomware. "The Cl0p Ransomware Gang, also known as TA505, reportedly began exploiting a previously unknown SQL injection vulnerability in Progress Software's managed file transfer solution known as MOVEit Transfer," the agencies said.

The Royal ransomware gang has begun testing a new encryptor called BlackSuit that shares many similarities with the operation's usual encryptor. Since its launch, Royal Ransomware has become one of the most active operations, responsible for numerous attacks on the enterprise.

Clop, the ransomware crew that has exploited the MOVEit vulnerability extensively to steal corporate data, has given victims a June 14 deadline to pay up or the purloined information will be leaked. Crucially, to steal the data, Clop exploited a deployment of MOVEit used by payroll services provider Zellis; British Airways et al are customers of Zellis, so when Clop broke into the payroll company's IT systems, the miscreants were able to snatch valuable employee data belonging to a host of orgs.

A number of ransomware gangs have stopped using malware to encrypt targets' files and have switched to a data theft/extortion approach to get paid; 0mega - a low-profile and seemingly not very active threat actor - seems to be among them. Evidence of its activities were first spotted roughly a year ago, when one victim - a UK-based electronics repair and refurbishment company - apparently refused to pay and the gang leaked company data on its dedicated leak site.

Get exclusive insights from a real ransomware negotiator who shares authentic stories from network hostage situations and how he managed them. In June 2021, following the ransomware attacks on the Colonial Pipeline and JBS, the Byden administration announced that ransomware was a threat to National Security.
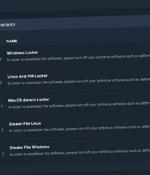
Threat actors associated with the Cyclops ransomware have been observed offering an information stealer malware that's designed to capture sensitive data from infected hosts. Cyclops ransomware is notable for targeting all major desktop operating systems, including Windows, macOS, and Linux.

The Clop ransomware gang has told BleepingComputer they are behind the MOVEit Transfer data-theft attacks, where a zero-day vulnerability was exploited to breach multiple companies' servers and steal data. Conducting attacks around holidays is a common tactic for the Clop ransomware operation, which has previously undertaken large-scale exploitation attacks during holidays when staff is at a minimum.