Security News

QNAP has warned customers today that most of its Network Attached Storage devices are vulnerable to attacks that would exploit a three-year-old critical PHP vulnerability allowing remote code execution. "A vulnerability has been reported to affect PHP versions 7.1.x below 7.1.33, 7.2.x below 7.2.24, and 7.3.x below 7.3.11. If exploited, the vulnerability allows attackers to gain remote code execution," QNAP explained in a security advisory released today.

Taiwan-based QNAP Systems is warning consumers and organizations using their network-attached storage appliances of a new DeadBolt ransomware campaign. Since NAS devices are often accessible remotely via the internet, criminals usually leverage software/firmware vulnerabilities or brute-force admin account passwords to gain access to them, pilfer and encrypt the files on them, then ask for a ransom to restore them.

This week, ech0raix ransomware has started targeting vulnerable QNAP Network Attached Storage devices again, according to user reports and sample submissions on the ID Ransomware platform. Ech0raix had hit QNAP customers in multiple large-scale waves starting with the summer of 2019 when the attackers brute-forced their way into Internet-exposed NAS devices.

QNAP is warning users about another wave of DeadBolt ransomware attacks against its network-attached storage devices - and urged customers to update their devices' QTS or QuTS hero operating systems to the latest versions. "Cybercriminals have taken notice of this dependence and now regularly update their known tools and routines to include network-attached storage devices to their list of targets, knowing full well that users rely on these devices for storing and backing up files in both modern homes and businesses," they wrote.

Network-attached storage vendor QNAP once again warned customers on Friday to secure their devices against a new campaign of attacks pushing DeadBolt ransomware. "QNAP recently detected a new DeadBolt ransomware campaign. According to victim reports so far, the campaign appears to target QNAP NAS devices running QTS 4.x," QNAP said today.
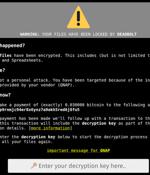
Taiwanese network-attached storage devices maker QNAP on Thursday warned its customers of a fresh wave of DeadBolt ransomware attacks. "QNAP urges all NAS users to check and update QTS to the latest version as soon as possible, and avoid exposing their NAS to the internet," QNAP said in an advisory.

Taiwan-based network-attached storage maker QNAP warned customers on Thursday to secure their devices against attacks pushing DeadBolt ransomware payloads."According to the investigation by the QNAP Product Security Incident Response Team, the attack targeted NAS devices using QTS 4.3.6 and QTS 4.4.1, and the affected models were mainly TS-x51 series and TS-x53 series," the NAS maker said.

QNAP, Taiwanese maker of network-attached storage devices, on Friday released security updates to patch nine security weaknesses, including a critical issue that could be exploited to take over an affected system. "A vulnerability has been reported to affect QNAP VS Series NVR running QVR," QNAP said in an advisory.

QNAP has released several security advisories today, one of them for a critical security issue that allows remote execution of arbitrary commands on vulnerable QVR systems, the company's video surveillance solution hosted on a NAS device. QNAP's advisory explains that the "Vulnerability has been reported to affect QNAP VS Series NVR running QVR. If exploited, this vulnerability allows remote attackers to run arbitrary commands."

Users of Synology and QNAP network-attached storage devices are advised to be on the lookout for patches for several critical vulnerabilities affecting Netatalk, an open-source implemention of the Apple Filing Protocol that allows Unix-like operating systems to serve file servers for Macs.Network-attached storage devices are usually used by small-to-medium businesses and home users for storing and sharing files and backups.