Security News

Hackers successfully infiltrated the computer system controlling a water treatment facility in the U.S. state of Florida and remotely changed a setting that drastically altered the levels of sodium hydroxide in the water. "At no time was there a significant effect on the water being treated, and more importantly the public was never in danger," Sheriff Gualtieri said in a statement.

U.S. law enforcement agencies are investigating a remote compromise of a Florida city's water plant, warning that the hackers tried to poison the water supply serving approximately 15,000 residents. The hack was spotted on February 5th - and neutralized - in real time by staff at the plant that supplies water to Oldsmar, a small city close to Tampa, Florida.

Researchers at Israel-based boutique cybersecurity consultancy JSOF this week disclosed the details of seven potentially serious DNS-related vulnerabilities that could expose millions of devices to various types of attacks. Its DNS subsystem "Provides a local DNS server for the network, with forwarding of all query types to upstream recursive DNS servers and caching of common record types."

Seven vulnerabilities affecting Dnsmasq, a caching DNS and DHCP server used in a variety of networking devices and Linux distributions, could be leveraged to mount DNS cache poisoning attack and/or to compromise vulnerable devices. "Some of the bigger users of Dnsmasq are Android/Google, Comcast, Cisco, Red Hat, Netgear, and Ubiquiti, but there are many more. All major Linux distributions offer Dnsmasq as a package, but some use it more than others, e.g., in OpenWRT it is used a lot, Red Hat use it as part of their virtualization platforms, Google uses it for Android hotspots, while, for example Ubuntu just has it as an optional package," Shlomi Oberman, CEO and researcher at JSOF, told Help Net Security.

"We see where troll feeding leads." Unfortunately not "Feeding" makes this troll change food source.

Microsoft issued guidance on how to mitigate a DNS cache poisoning vulnerability reported by security researchers from the University of California and Tsinghua University. Successfully exploiting the vulnerability could allow attackers to use modified DNS records to redirect a target to a malicious website under their control as part of DNS spoofing attacks.

Jack Wallen walks you through the process of putting in place a temporary fix against SAD DNS for your Linux servers and desktops. There's a new DNS cache poisoning threat in town and it goes by the name of Side-channel AttackeD DNS. This new attack works like so: SAD DNS makes it possible for hackers to reroute traffic destined to a specific domain to a server under their control.
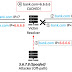
A group of academics from the University of California and Tsinghua University has uncovered a series of critical security flaws that could lead to a revival of DNS cache poisoning attacks. The effectiveness of such attacks has taken a hit in part due to protocols such as DNSSEC that creates a secure domain name system by adding cryptographic signatures to existing DNS records and randomization-based defenses that allow the DNS resolver to use a different source port and transaction ID for every query.

Researchers from Tsinghua University and the University of California have identified a new method that can be used to conduct DNS cache poisoning attacks. DNS cache poisoning attacks refer to polluting this very cache existing on intermediary servers.

A team of German cybersecurity researchers has discovered a new cache poisoning attack against web caching systems that could be used by an attacker to force a targeted website into delivering...