Security News

A rendering technique affecting the world's leading messaging and email platforms, including Instagram, iMessage, WhatsApp, Signal, and Facebook Messenger, allowed threat actors to create legitimate-looking phishing messages for the past three years. The vulnerabilities are rendering bugs resulting in the apps' interface incorrectly displaying URLs with injected RTLO Unicode control characters, making the user vulnerable to URI spoofing attacks.

Modern phishing kits sold on cybercrime forums as off-the-shelve packages feature multiple, sophisticated detection avoidance and traffic filtering systems to ensure that internet security solutions won't mark them as a threat. Most of these websites are built using phishing kits that feature brand logos, realistic login pages, and in cases of advanced offerings, dynamic webpages assembled from a set of basic elements.

The novel phishing technique, described last week by a penetration tester and security researcher who goes by the handle mr. The concocted popups simulate a browser window within the browser, spoofing a legitimate domain and making it possible to stage convincing phishing attacks.
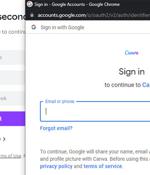
A novel phishing technique called browser-in-the-browser attack can be exploited to simulate a browser window within the browser in order to spoof a legitimate domain, thereby making it possible to stage convincing phishing attacks. "Combine the window design with an iframe pointing to the malicious server hosting the phishing page, and it's basically indistinguishable," mrd0x said in a technical write-up published last week.

A phishing kit has been released that allows red teamers and wannabe cybercriminals to create effective single sign-on phishing login forms using fake Chrome browser windows. Threat actors have attempted to create these fake SSO windows using HTML, CSS, and JavaScript in the past, but there is usually something a little off about the windows, making them look suspicious.

Bypassing defenses built into the user's browser to fool them into trusting a malicious page tends to be difficult in the absence of an exploitable vulnerability, thanks to browser security mechanisms including Content Security Policy settings and the Same-origin policy security model. The BitB attack extends this technique by creating an entirely fabricated browser window, including trust signals like a locked padlock icon and a known URL. You think you're seeing a real popup window, but it's actually just faked within the page, and ready to capture your credentials.

In addition to dealing with threats designed to take advantage of the war in Ukraine, companies and governments face fresh attacks from new and existing vulnerabilities on many fronts. CISA added 15 new vulnerabilities to its Known Exploited Vulnerabilities Catalog this week to draw attention to vulnerabilities bad actors are actively exploiting.

Security firm Avanan on Thursday published its latest analysis of a phishing technique that builds on the internet community's familiarity with CAPTCHA challenges to amplify the effectiveness of deceptions designed to capture sensitive data. CAPTCHA puzzles, such as Google's reCAPTCHA, can act as a roadblock for these scanners because the filters can't solve the puzzles.

Large-scale phishing activity using hundreds of domains to steal credentials for Naver, a Google-like online platform in South Korea, shows infrastructure overlaps linked to the TrickBot botnet. Security researchers at cyber intelligence company Prevailion earlier this year identified a massive phishing operation focused on collecting credentials of Naver users.

Large-scale phishing activity using hundreds of domains to steal credentials for Naver, a Google-like online platform in South Korea, shows infrastructure overlaps linked to the TrickBot botnet. Security researchers at cyber intelligence company Prevailion earlier this year identified a massive phishing operation focused on collecting credentials of Naver users.