Security News

"We immediately identified and isolated the attack to effectively limit its impact and have contacted those customers affected. Customers who have not received an email have not been impacted" - Revolut. According to the breach disclosure to the State Data Protection Inspectorate in Lithuania, where Revolut has a banking license, 50,150 customers have been impacted.

A novel phishing campaign is underway, targeting Greeks with phishing sites that mimic the state's official tax refund platform and steal credentials as they type them. The threat actors are sending phishing emails claiming that the Hellenic Tax Office has calculated a tax return amounting to 634 Euros but failed to send the funds to the beneficiary's bank account due to validation issues.

An Iranian-aligned hacking group uses a new, elaborate phishing technique where they use multiple personas and email accounts to lure targets into thinking its a realistic email conversation. The attackers send an email to targets while CCing another email address under their control and then respond from that email, engaging in a fake conversation.

The Lampion malware is being distributed in greater volumes lately, with threat actors abusing WeTransfer as part of their phishing campaigns. In a new campaign observed by email security firm Cofense, Lampion operators are sending phishing emails from compromised company accounts urging users to download a "Proof of Payment" document from WeTransfer.
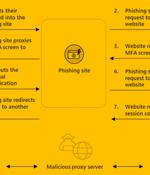
A new phishing-as-a-service toolkit dubbed EvilProxy is being advertised on the criminal underground as a means for threat actors to bypass two-factor authentication protections employed against online services. "EvilProxy actors are using reverse proxy and cookie injection methods to bypass 2FA authentication - proxifying victim's session," Resecurity researchers said in a Monday write-up.

Resecurity has recently identified a new Phishing-as-a-Service called EvilProxy advertised in the Dark Web. While the incident with Twilio is solely related to the supply chain, cybersecurity risks obviously lead to attacks against downstream targets, the productized underground service like EvilProxy enables threat actors to attack users with enabled MFA on the largest scale without the need to hack upstream services.

A reverse-proxy Phishing-as-a-Service platform called EvilProxy has emerged, promising to steal authentication tokens to bypass multi-factor authentication on Apple, Google, Facebook, Microsoft, Twitter, GitHub, GoDaddy, and even PyPI. The service enables low-skill threat actors who don't know how to set up reverse proxies to steal online accounts that are otherwise well-protected. The difference between these phishing frameworks and EvilProxy is that the latter is far simpler to deploy, offers detailed instructional videos and tutorials, a user-friendly graphical interface, and a rich selection of cloned phishing pages for popular internet services.
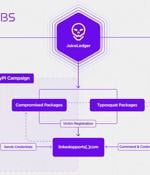
More details have emerged about the operators behind the first-known phishing campaign specifically aimed at the Python Package Index, the official third-party software repository for the programming language. The attacks received a significant facelift last month when the JuiceLedger actors targeted PyPi package contributors in a phishing campaign, resulting in the compromise of three packages with malware.

Blue badges are highly coveted as Instagram provides them to accounts it verified to be authentic, representing a public figure, celebrity, or brand. The spear emails in the recently observed phishing campaign inform recipients that they Instagram reviewed their accounts and deemed them eligible for a blue badge.

Brian Krebs is reporting on a clever PayPal phishing scam that uses legitimate PayPal messaging. Basically, the scammers use the PayPal invoicing system to send the email.