Security News

An updated version of an information-stealing malware called Rhadamanthys is being used in phishing campaigns targeting the oil and gas sector. "The phishing emails use a unique vehicle incident...
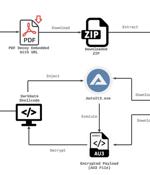
The threat actor known as TA558 has been attributed to a new massive phishing campaign that targets a wide range of sectors in Latin America with the goal of deploying Venom RAT. The attacks...

Google has started automatically blocking emails sent by bulk senders who don't meet stricter spam thresholds and authenticate their messages as required by new guidelines to strengthen defenses against spam and phishing attacks. Non-compliance may result in email delivery issues, including rejected emails or emails being automatically sent to recipients' spam folders.

A sophisticated phishing-as-a-service (PhaaS) platform called Darcula has set its sights on organizations in over 100 countries by leveraging a massive network of more than 20,000 counterfeit...

One thing that makes the service stand out is that it approaches the targets using the Rich Communication Services protocol for Google Messages and iMessage instead of SMS for sending phishing messages. "The Darcula platform has been used for numerous high-profile phishing attacks over the last year, including messages received on both Apple and Android devices in the UK, as well as package scams impersonating United States Postal Service highlighted in numerous posts on Reddit's /r/phishing." - Netcraft.

Those quirky choices aside, the platform is a serious threat: it allows criminals that are not that tech savvy to automate many of the steps needed to launch a phishing campaign, thus lowering the barrier to entry in the world of cybercrime. Its use of JavaScript, React, Docker, and Harbor Its capability to update phishing sites with new features and anti-detection measures without having to remove and re-install the phishing kit.
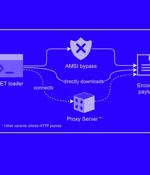
A new phishing campaign has been observed leveraging a novel loader malware to deliver an information stealer and keylogger called Agent Tesla. Trustwave SpiderLabs said it identified a phishing...

Cybercriminals have been increasingly using a new phishing-as-a-service platform named 'Tycoon 2FA' to target Microsoft 365 and Gmail accounts and bypass two-factor authentication protection. Tycoon 2FA attacks involve a multi-step process where the threat actor steals session cookies by using a reverse proxy server hosting the phishing web page, which intercepts the victim's input and relays them to the legitimate service.

The Iran-affiliated threat actor tracked as MuddyWater (aka Mango Sandstorm or TA450) has been linked to a new phishing campaign in March 2024 that aims to deliver a legitimate Remote Monitoring...

The Kremlin's cyberspies targeted German political parties in a phishing campaign that used emails disguised as dinner party invitations, according to Mandiant. Russia's Cozy Bear, also known as APT29 and Midnight Blizzard, engineered the messages to infect marks' Windows PCs with a backdoor first observed in January and dubbed WINELOADER. These were intended to provide long-term access to the political parties' networks and data, the Google-backed security biz asserted on Friday.