Security News

A high-severity Palo Alto Networks denial-of-service vulnerability has been exploited by miscreants looking to launch DDoS attacks, and several of the affected products won't have a patch until next week.The vulnerability, tracked as CVE-2022-0028, received an 8.6 out of 10 CVSS score, and it affects PAN OS, the operating system in Palo Alto Networks' network security products.

Palo Alto Networks has issued a security advisory warning of an actively exploited high-severity vulnerability impacting PAN-OS, the operating system used by the company's networking hardware products. The issue, tracked as CVE-2022-0028, is an URL filtering policy misconfiguration that could allow an unauthenticated, remote attacker to carry out amplified TCP denial-of-service attacks.

Founded back in 2005, Palo Alto Networks is a cybersecurity giant that has earned the trust of the business community thanks to its impressive track record. The Palo Alto Networks Cybersecurity Fundamentals course helps you gain that same level of credibility, with 27 tutorials working towards official certification.

American cybersecurity company Palo Alto Networks warned customers on Wednesday that some of its firewall, VPN, and XDR products are vulnerable to a high severity OpenSSL infinite loop bug disclosed three weeks ago.Even though the OpenSSL team released a patch two weeks ago when it publicly disclosed the bug, customers will have to wait until later this month when Palo Alto Networks plans to release security updates.

EXCLUSIVE: A bug in the support dashboard of Palo Alto Networks exposed thousands of customer support tickets to an unauthorized individual, BleepingComputer has learned. The exposed information included, names and contact information of the person creating support tickets, conversations between Palo Alto Networks staff members and the customer.
A new zero-day vulnerability has been disclosed in Palo Alto Networks GlobalProtect VPN that could be abused by an unauthenticated network-based attacker to execute arbitrary code on affected devices with root user privileges. Successful exploitation of the flaw necessitates that the attacker strings it with a technique known as HTTP smuggling to achieve remote code execution on the VPN installations, not to mention have network access to the device on the GlobalProtect service default port 443.

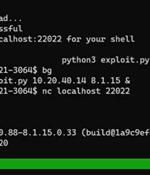
Critical RCE in Palo Alto Networks firewalls revealed, patch ASAP!The existence of a critical RCE vulnerability affecting certain versions of Palo Alto Networks firewalls using the GlobalProtect Portal VPN has been revealed by a cybersecurity company that exploited it during red team engagements for the last 12 months. Vulnerabilities in Nucleus NET TCP/IP stack could lead to real-world damageResearchers have unearthed 13 vulnerabilities affecting the Nucleus NET TCP/IP stack and have demonstrated how attackers could exploit them to cause serious real-world damage.

The existence of a critical RCE vulnerability affecting certain versions of Palo Alto Networks firewalls using the GlobalProtect Portal VPN has been revealed by a cybersecurity company that exploited it during red team engagements for the last 12 months. The vulnerability has been patched, but since there are still over 10,000 vulnerable internet-facing installations out there, Randori will refrain from publishing technical details related to the vulnerability for a month, to give affected organizations enough time to patch.

Palo Alto Networks has issued a patch for a CVSS 9.8-rated buffer overflow affecting a VPN component of its widely used firewall software, warning that the flaw allows unauthenticated attackers to execute arbitrary code on unpatched appliances. "A memory corruption vulnerability exists in Palo Alto Networks GlobalProtect portal and gateway interfaces that enables an unauthenticated network-based attacker to disrupt system processes and potentially execute arbitrary code with root privileges," said the company in an advisory published this week.

Researchers have developed a working exploit to gain remote code execution via a massive vulnerability in a security appliance from Palo Alto Networks, potentially leaving more than 70,000 vulnerable firewalls with their goods exposed to the internet. The Randori Attack Team found the zero day a year ago, developed a working exploit and used it against Randori customers over the past year.