Security News

Two malicious packages discovered in the npm package repository have been found to conceal an open source information stealer malware called TurkoRat. The findings once again underscore the ongoing risk of threat actors orchestrating supply chain attacks via open source packages and baiting developers into downloading potentially untrusted code.

Developers who use GitHub Actions to build software packages for the npm registry can now add a command flag that will publish details about the code's origin. It's often used by software developers to mechanize the build process for packages distributed through the company's npm registry, which hosts more than two million of these modular libraries.

Threat actors are flooding the npm open source package repository with bogus packages that briefly even resulted in a denial-of-service attack. "The threat actors create malicious websites and publish empty packages with links to those malicious websites, taking advantage of open-source ecosystems' good reputation on search engines," Checkmarx's Jossef Harush Kadouri said in a report published last week.

Attackers are exploiting the good reputation and "Openness" of the popular public JavaScript software registry NPM to deliver malware and scams, but are also simultaneously and inadvertently launching DoS attacks against the service. Malicious package on NPM pointing to a site serving malware.

They existed simply as placeholders for README files that included the final links that the crooks wanted people to click on. These links typically including referral codes that would net the scammers a modest reward, even if the person clicking through was doing so simply to see what on earth was going on.
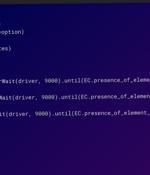
In what's a continuing assault on the open source ecosystem, over 15,000 spam packages have flooded the npm repository in an attempt to distribute phishing links. "The packages were created using automated processes, with project descriptions and auto-generated names that closely resembled one another," Checkmarx researcher Yehuda Gelb said in a Tuesday report.

A popular npm package with more than 3.5 million weekly downloads has been found vulnerable to an account takeover attack. "The package can be taken over by recovering an expired domain name for one of its maintainers and resetting the password," software supply chain security company Illustria said in a report.

A new set of 16 malicious NPM packages are pretending to be internet speed testers but are, in reality, coinminers that hijack the compromised computer's resources to mine cryptocurrency for the threat actors. The packages were uploaded onto NPM, an online repository containing over 2.2 million open-source JavaScript packages shared among software developers to speed up the coding process.
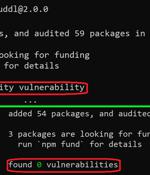
New findings from cybersecurity firm JFrog show that malware targeting the npm ecosystem can evade security checks by taking advantage of an "Unexpected behavior" in the npm command line interface tool. Npm CLI's install and audit commands have built-in capabilities to check a package and all of its dependencies for known vulnerabilities, effectively acting as a warning mechanism for developers by highlighting the flaws.
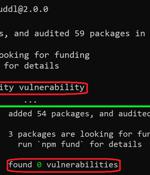
New findings from cybersecurity firm JFrog show that malware targeting the npm ecosystem can evade security checks by taking advantage of an "Unexpected behavior" in the npm command line interface tool. Npm CLI's install and audit commands have built-in capabilities to check a package and all of its dependencies for known vulnerabilities, effectively acting as a warning mechanism for developers by highlighting the flaws.