Security News

Chinese-speaking users are the target of an ongoing campaign that distributes malware known as ValleyRAT. "ValleyRAT is a multi-stage malware that utilizes diverse techniques to monitor and control its victims and deploy arbitrary plugins to cause further damage," Fortinet FortiGuard Labs researchers Eduardo Altares and Joie Salvio said. The attack sequence is a multi-stage process that starts with a first-stage loader that impersonates legitimate applications like Microsoft Office to make them appear harmless.

This reality requires the adoption of a multi-factor authentication policy within organizations. Multi-factor authentication is a powerful tool for safeguarding sensitive data from unauthorized access.
A new sophisticated cyber attack has been observed targeting endpoints geolocated to Ukraine with an aim to deploy Cobalt Strike and seize control of the compromised hosts. The attack chain, per...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.
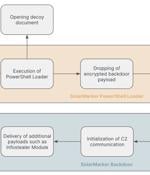
The persistent threat actors behind the SolarMarker information-stealing malware have established a multi-tiered infrastructure to complicate law enforcement takedown efforts, new findings from...

Starting in July, Microsoft will begin gradually enforcing multi-factor authentication for all users signing into Azure to administer resources. "Service principals, managed identities, workload identities, and similar token-based accounts used for automation are excluded. Microsoft is still gathering customer input for certain scenarios such as break-glass accounts and other special recovery processes," explained Azure product manager Naj Shahid.

Setting up MFA can seem daunting for consumers just beginning to clean up their security postures. In this Help Net Security video, Larry Kinkaid, Manager, Cybersecurity Consulting at BARR Advisory, shares tips for consumers who need simple, accessible ways to secure their private data.

Google is rolling out a new Workspace feature that requires multiple admins to approve high-risk setting changes to prevent unauthorized or accidental modifications that could reduce security. Google Workspace is a comprehensive suite of cloud-based productivity and collaboration tools, integrating services such as Gmail, Google Drive, Google Docs, Sheets, Slides, Google Meet, and Google Calendar, offering a unified solution for businesses, educational institutions, and individuals.

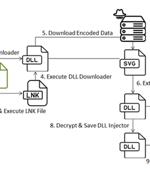
Cybersecurity researchers have discovered an intricate multi-stage attack that leverages invoice-themed phishing decoys to deliver a wide range of malware such as Venom RAT, Remcos RAT, XWorm,...

MFA software solutions provide multi-factor authentication for individual end-users, organizational workforces and customer-facing applications. Software Solution category Authentication types Hosting options Pricing Google Authenticator Individual MFA Mobile app, software token, mobile push, risk-based Cloud-based Free Cisco Duo Workforce MFA Mobile app, software token, hardware token, mobile push, WebAuthn, biometric Cloud-based Free MFA for up to 10 users; plans start at $3/user/month.