Security News

How to use DuckDuckGo on your PC and mobile devices. To install the DuckDuckGo extension, open Chrome or Firefox and browse to the DuckDuckGo home page.

Roaming Mantis mobile smishing campaign spreads, gets updated features. The mobile malware campaign known as Roaming Mantis largely left the news cycle after making a splash in 2018, but Kaspersky is reporting that some new life has been breathed into the campaign in the form of new features and new targets: This time it's set its sights on France and Germany.

Bring a burner to the Olympics, and other mobile device travel safety tips. In order to know what's awaiting you in regards to privacy laws, Turner recommends checking the U.S. State Department Travel Advisory website for a quick rundown of any legal differences you may run into while abroad. As for universally applicable safety tips for protecting your mobile devices and data, Turner and Forrester security and risk analyst Allie Mellen both have tips.

Nation states will ramp up mobile cyber attacks; hyperscalers will mimic Google and introduce powerful proprietary encryption protocols; and new edge clouds could make the last mile vulnerable. Mobile industry trends in 2022 State-sponsored cyber attacks accelerate and evolve.
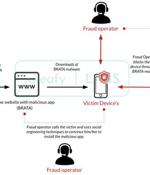
The Android malware tracked as BRATA has been updated with new features that grants it the ability to track device locations and even perform a factory reset in an apparent bid to cover up fraudulent wire transfers. "What makes Android RAT so interesting for attackers is its capability to operate directly on the victim devices instead of using a new device," Cleafy researchers noted in December 2021.

Mobile application security testing will be a priority for any organization with a mobile app in 2022. When mobile app security includes frequent testing to obtain real feedback, mobile app developers are better prepared to identify and mitigate mobile app security threats and vulnerabilities.

The global mobile device management market size to grow from $5.5 billion in 2021 to $20.4 billion by 2026, at a Compound Annual Growth Rate of 29.8% during the forecast period, according to MarketsandMarkets. Mobile device management solutions allow IT teams and admins to control and distribute security policies to mobile devices accessing sensitive corporate data in their organizations, ensuring the corporate network is secure.

So how can organizations overcome the sudden increase in security threats and regain the upper hand against bad actors with fewer resources than ever before? Increasingly, it looks like zero-trust will become the ideal approach for doing more with less, because ultimately, it's the users and their cyber-hygiene that's the first line in phishing defense. As anyone, no matter how technically savvy, is at risk of falling victim to phishing attacks, it's vital that organizations rethink their approach to security as a whole to combat these threats.

The mobile security software market is expected to witness significant growth in the coming years with the increased adoption of mobile devices. Technavio expects the global mobile security software market to grow by $2.75 billion between 2020 and 2025, expanding at a CAGR of 9.68% during the forecast period.

T-Mobile confirmed that recent reports of a new data breach are linked to notifications sent to a "Very small number of customers" who fell victim to SIM swap attacks. SIM swapping makes it possible for attackers to take control of a target's mobile phone number by tricking or bribing the carrier's employees to reassign the numbers to attacker-controlled SIM cards.