Security News

Microsoft has added SMTP MTA Strict Transport Security support to Exchange Online to ensure Office 365 customers' email communication integrity and security. This new standard strengthens Exchange Online email security and solves several SMTP security problems, including expired TLS certificates, the lack of support for secure protocols, and certificates not issued by trusted third parties or matching server domain names.
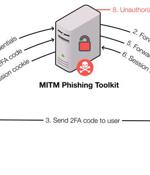
The findings come from a new study undertaken by a group of researchers from Stony Brook University and Palo Alto Networks, who have demonstrated a new fingerprinting technique that makes it possible to identify MitM phishing kits in the wild by leveraging their intrinsic network-level properties, effectively automating the discovery and analysis of phishing websites. Dubbed "PHOCA" - named after the Latin word for "Seals" - the tool not only facilitates the discovery of previously unseen MitM phishing toolkits, but also be used to detect and isolate malicious requests coming from such servers.

The Kubernetes Product Security Committee has provided advice on how to temporarily block attackers from exploiting a vulnerability that could enable them to intercept traffic from other pods in multi-tenant Kubernetes clusters in man-in-the-middle attacks. CVE-2020-8554 is a design flaw that impacts all Kubernetes versions, with multi-tenant clusters that allow tenants to create and update services and pods being the most vulnerable to attacks.

Microsoft is working on adding SMTP MTA Strict Transport Security support to Exchange Online to ensure Office 365 customers' email communication security and integrity. Once MTA-STS is available in Office 365 Exchange Online, emails sent by users via Exchange Online will only one delivered using connections with both authentication and encryption, protecting against both email interception and attacks.

According to the SAM IoT Security Lab, the FortiGate SSL-VPN client only verifies that the certificate used for client authentication was issued by Fortinet or another trusted certificate authority. "Therefore, an attacker can easily present a certificate issued to a different FortiGate router without raising any flags, and implement a man-in-the-middle attack," researchers wrote, in an analysis on Thursday.

A security vulnerability in the Cross-Transport Key Derivation of devices supporting both Bluetooth BR/EDR and LE could allow an attacker to overwrite encryption keys, researchers have discovered. The implementation of CTKD in older versions of the specification "May permit escalation of access between the two transports with non-authenticated encryption keys replacing authenticated keys or weaker encryption keys replacing stronger encryption keys," the Bluetooth Special Interest Group explains.

Setting out to find out, the researcher turned to the main domain registrars - GoDaddy, Namecheap and even Google Domains - to first see if he could snag appropriate URLs. "The great thing about using a proxy is that my domain's links previews, in every single platform, fetches Google Translate's exact description while pointing to my link," the researcher explained.

A vulnerability in Avast's anti-tracking solution could allow malicious actors to perform man-in-the-middle attacks on HTTPS traffic, a security researcher has discovered. The security flaw, which impacts both Avast and AVG AntiTrack, as they share underlying code, resides in the manner in which the software filters HTTPS traffic.

Researchers uncovers “ultimate man-in-the-middle attack” that used an elaborate spoofing campaign to fool a Chinese VC firm and rip off an emerging business.

This new skimming/phishing hybrid threat tactic means that even stores that send customers to external payment processors are vulnerable.