Security News

OpenSSH has released security updates addressing two vulnerabilities, a machine-in-the-middle (MitM) and a denial of service flaw, with one of the flaws introduced over a decade ago. [...]

The Russian hacking group tracked as APT29 (aka "Midnight Blizzard") is using a network of 193 remote desktop protocol proxy servers to perform man-in-the-middle (MiTM) attacks to steal data and...

qBittorrent has addressed a remote code execution flaw caused by the failure to validate SSL/TLS certificates in the application's DownloadManager, a component that manages downloads throughout...

Cybersecurity researchers have discovered a security vulnerability in the RADIUS network authentication protocol called BlastRADIUS that could be exploited by an attacker to stage Mallory-in-the-middle attacks and bypass integrity checks under certain circumstances. "The RADIUS protocol allows certain Access-Request messages to have no integrity or authentication checks," InkBridge Networks CEO Alan DeKok, who is the creator of the FreeRADIUS Project, said in a statement.

Researchers demonstrated how they could conduct a Man-in-the-Middle phishing attack to compromise Tesla accounts, unlocking cars, and starting them. The attack works on the latest Tesla app, version 4.30.6, and Tesla software version 11.1 2024.2.7.

Professors at the University of South Australia and Charles Sturt University have developed an algorithm to detect and intercept man-in-the-middle attacks on unmanned military robots. MitM attacks are a type of cyberattack where the data traffic between two parties, in this case, the robot and its legitimate controllers, is intercepted either to eavesdrop or to inject false data in the stream.

The UK law enforcement office SEROCU, short for South East Regional Organised Crime Unit, this week reported the peculiar tale of one Ashley Liles, the literal Man in the Middle whom we referred to in the headline. These days, we usually expand the jargon term MitM to mean Manipulator in the Middle, not merely to avoid the gendered term "Man", but also because many, if not most, MitM attacks these days are performed by machines.

Four vulnerabilities in the widely adopted 'Stacked VLAN' Ethernet feature allows attackers to perform denial-of-service or man-in-the-middle attacks against network targets using custom-crafted packets. Stacked VLANs, also known as VLAN Stacking, is a feature in modern routers and switches that allows companies to encapsulate multiple VLAN IDs into a single VLAN connection shared with an upstream provider.
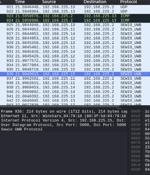
Researchers have disclosed multiple vulnerabilities impacting Ultra-wideband Real-time Locating Systems, enabling threat actors to launch adversary-in-the-middle attacks and tamper with location data. "If a threat actor exploits these vulnerabilities, they have the ability to tamper with safety zones designated by RTLS to protect workers in hazardous areas."

Security researchers have uncovered multiple vulnerabilities impacting UWB RTLS, enabling threat actors to conduct man-in-the-middle attacks and manipulate tag geo-location data. Nozomi analysts focused on the Sewio Indoor Tracking RTLS UWB Wi-Fi kit and Avalue Renity Artemis Enterprise kit, two widely used RTLS solutions that support the safety functionalities described above.