Security News

The threat actors behind the HiatusRAT malware have returned from their hiatus with a new wave of reconnaissance and targeting activity aimed at Taiwan-based organizations and a U.S. military procurement system. Besides recompiling malware samples for different architectures, the artifacts are said to have been hosted on new virtual private servers, Lumen Black Lotus Labs said in a report published last week.

The NSA discovered the intrusion in 2020-we don't know how-and alerted the Japanese. The hackers had deep, persistent access and appeared to be after anything they could get their hands on-plans, capabilities, assessments of military shortcomings, according to three former senior U.S. officials, who were among a dozen current and former U.S. and Japanese officials interviewed, who spoke on the condition of anonymity because of the matter's sensitivity.

Two US Navy service members appeared in federal court Thursday accused of espionage and stealing sensitive military information for China in separate cases. According to Uncle Sam, Wei had been handing off photos, videos, and technical manuals about US Navy ships and systems since February 2022.

As if attacks from China weren't enough, one of the Air Force's own has reportedly gone rogue The US government is fighting a pair of cyber security incidents, one involving Chinese spies who...
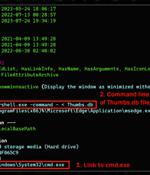
An ongoing cyber attack campaign has set its sights on Korean-speaking individuals by employing U.S. Military-themed document lures to trick them into running malware on compromised systems. Cybersecurity firm Securonix is tracking the activity under the name STARK#MULE. "Based on the source and likely targets, these types of attacks are on par with past attacks stemming from typical North Korean groups such as APT37 as South Korea has historically been a primary target of the group, especially its government officials," security researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov said in a report shared with The Hacker News.

Mil US military addresses were actually directed at. As a result of that one-character typo, medical data, identity documents, maps of military installations, travel itineraries, bookings for high-ranking military leaders, and more have been fired off at.

A North Korean satellite allegedly designed for reconnaissance was not viable for its alleged intended purpose, according to South Korea's military on Wednesday. North Korea attempted to put the satellite into orbit on May 31, but it instead plunged into the sea soon after it was launched.

A Florida man has pleaded guilty to importing and selling counterfeit Cisco networking equipment to various organizations, including education, government agencies, healthcare, and the military. A U.S. Department of Justice announcement published yesterday says Aksoy pleaded guilty in the U.S. District Court of New Jersey, admitting that he defrauded many people and companies by selling them low-quality equipment made to appear as new Cisco models.

The Dark Pink APT hacking group continues to be very active in 2023, observed targeting government, military, and education organizations in Indonesia, Brunei, and Vietnam. Despite the previous exposure by Group-IB, Dark Pink has not shown any signs of slowing down, and the company says it identified at least five attacks perpetrated by the group following the publication of the previous report.
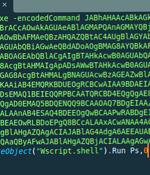
A previously undetected advanced persistent threat actor dubbed Red Stinger has been linked to attacks targeting Eastern Europe since 2020. Red Stinger overlaps with a threat cluster Kaspersky revealed under the name Bad Magic last month as having targeted government, agriculture, and transportation organizations located in Donetsk, Lugansk, and Crimea last year.