Security News
As many as five security flaws have been disclosed in Netgear RAX30 routers that could be chained to bypass authentication and achieve remote code execution. "Successful exploits could allow attackers to monitor users' internet activity, hijack internet connections, and redirect traffic to malicious websites or inject malware into network traffic," Claroty security researcher Uri Katz said in a report.

A new, stealthier variant of the Linux malware 'BPFDoor' has been discovered, featuring more robust encryption and reverse shell communications. BPFDoor is a stealthy backdoor malware that has been active since at least 2017 but was only discovered by security researchers around 12 months ago.

Black Hat Asia Threat groups have infected millions of Androids worldwide with malicious firmware before the devices have even been shipped from their manufacturers, according to Trend Micro researchers at Black Hat Asia. The mainly mobile devices, but also smartwatches, TVs and more, have their manufacturing outsourced to an original equipment manufacturer, a process the researchers say makes them easily infiltrated.

New samples of the RapperBot botnet malware have added cryptojacking capabilites to mine for cryptocurrency on compromised Intel x64 machines. Researchers at Fortinet's FortiGuard Labs have been tracking RapperBot activity since June 2022 and reported that the Mirai-based botnet focused on brute-forcing Linux SSH servers to recruit them for launching distributed denial-of-service attacks.

A recently spotted malvertising campaign tricked users with an in-browser Windows update simulation to deliver the Aurora information stealing malware. Written in Golang, Aurora has been available on various hacker forums for more than a year, advertised as an info stealer with extensive capabilities and low antivirus detection.

Reuters is reporting that the FBI "Had identified and disabled malware wielded by Russia's FSB security service against an undisclosed number of American computers, a move they hoped would deal a death blow to one of Russia's leading cyber spying programs." The headline says that the FBI "Sabotaged" the malware, which seems to be wrong.
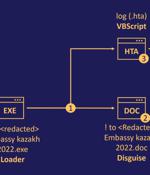
Government organizations in Central Asia are the target of a sophisticated espionage campaign that leverages a previously undocumented strain of malware dubbed DownEx. The Romanian cybersecurity firm said it first detected the malware in a highly targeted attack aimed at foreign government institutions in Kazakhstan in late 2022.

The US Government has been investigating Snake and Snake-related malware tools for nearly 20 years, and has monitored FSB officers assigned to Turla conducting daily operations using Snake from a known FSB facility in Ryazan, Russia. Although Snake has been the subject to several cybersecurity industry reports throughout its existence, Turla has applied numerous upgrades and revisions, and selectively deployed it, all to ensure that Snake remains Turla's most sophisticated long-term cyberespionage malware implant.

Even more alarming are the revelations in this year's report about browser session cookies - unquestionably the most prized data exfiltrated by malware. SpyCloud recaptured 1.87 billion malware cookie records tied to Fortune 1000 employees.

The FBI has cut off a network of Kremlin-controlled computers used to spread the Snake malware which, according to the Feds, has been used by Russia's FSB to steal sensitive documents from NATO members for almost two decades. After identifying and stealing sensitive files on victims' devices, Turla exfiltrated them through a covert network of unwitting Snake-compromised computers in the US. In effect, Snake can infect Windows, Linux, and macOS systems, and use those network nodes to pass data stolen from victims along to the software nasty's Russian spymasters.