Security News

A new PowerShell malware script named 'PowerDrop' has been discovered to be used in attacks targeting the U.S. aerospace defense industry. PowerDrop was discovered by Adlumin, who last month found a sample of the malware in the network of a defense contractor in the U.S. The firm reports that PowerDrop uses PowerShell and WMI to create a persistent RAT on the breached networks.

Cybersecurity firm Kaspersky has released a tool to detect if Apple iPhones and other iOS devices are infected with a new 'Triangulation' malware. Although the malware analysis is still underway, the cybersecurity firm noted that the 'Operation Triangulation' malware campaign uses an unknown zero-day exploit on iMessage to perform code execution without user interaction and elevated privileges.

The SpinOk malware was found in a new batch of Android apps on Google Play, reportedly installed an additional 30 million times. SpinOk was first discovered by Dr. Web late last month in a set of a hundred apps that had been collectively downloaded over 421 million times.

The Qbot malware operation - which started more than a decade ago as banking trojan only to evolve into a backdoor and a delivery system for ransomware and other threats - continues to deftly adapt its techniques to stay ahead of security pros, according to a new report. Most recently, the operators behind Qbot - also known as Qakbot and Pinkslipbot - this year have shown new methods for delivering malware and a highly adaptable command-and-control infrastructure, with a quarter of those used being active for only a day, researchers with Lumen's Black Lotus Labs threat intelligence group write.

Online sellers are targeted in a new campaign to push the Vidar information-stealing malware, allowing threat actors to steal credentials for more damaging attacks. The new campaign launched this week, with threat actors sending complaints to online store admins through email and website contact forms.
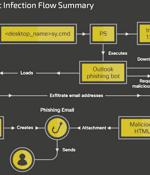
Spanish-speaking users in Latin America have been at the receiving end of a new botnet malware dubbed Horabot since at least November 2020. "Horabot enables the threat actor to control the victim's Outlook mailbox, exfiltrate contacts' email addresses, and send phishing emails with malicious HTML attachments to all addresses in the victim's mailbox," Cisco Talos researcher Chetan Raghuprasad said.

An analysis of the "Evasive and tenacious" malware known as QBot has revealed that 25% of its command-and-control servers are merely active for a single day. What's more, 50% of the servers don't remain active for more than a week, indicating the use of an adaptable and dynamic C2 infrastructure, Lumen Black Lotus Labs said in a report shared with The Hacker News.

A previously unknown advanced persistent threat is targeting iOS devices as part of a sophisticated and long-running mobile campaign dubbed Operation Triangulation that began in 2019. "The targets are infected using zero-click exploits via the iMessage platform, and the malware runs with root privileges, gaining complete control over the device and user data," Kaspersky said.

A stealthy remote access trojan named 'SeroXen' has recently gained popularity as cybercriminals begin using it for its low detection rates and powerful capabilities. AT&T reports that the malware is sold under the guise of a legitimate remote access tool for Windows 11 and 10 for $15/month or a single "Lifetime" license payment of $60. While marketed as a legitimate program, the Flare Systems cyber intel platform has shown that SeroXen is promoted as a remote access trojan on hacking forums.

Network and email security firm Barracuda today revealed that a recently patched zero-day vulnerability had been exploited for at least seven months to backdoor customers' Email Security Gateway appliances with custom malware and steal data. The company says an ongoing investigation found that the bug was first exploited in October 2022 to gain access to "a subset of ESG appliances" and deploy backdoors designed to provide the attackers with persistent access to the compromised systems.