Security News

A previously undocumented Windows-based information stealer called ThirdEye has been discovered in the wild with capabilities to harvest sensitive data from infected hosts. The arrival vector for the malware is presently unknown, although the nature of the lure points to it being used in a phishing campaign.
A new process injection technique dubbed Mockingjay could be exploited by threat actors to bypass security solutions to execute malicious code on compromised systems. Process injection is an attack method that allows adversaries to inject code into processes in order to evade process-based defenses and elevate privileges.

Security researchers discovered a new malicious tool they named PindOS that delivers the Bumblebee and IcedID malware typically associated with ransomware attacks. PindOS is a simple JavaScript malware dropper that appears to be built specifically to fetch the next-stage payloads that deliver the attackers' final payload. Simple JavaScript malware dropper.

A trojanized installer for the popular Super Mario 3: Mario Forever game for Windows has been infecting unsuspecting players with multiple malware infections. Super Mario 3: Mario Forever is a free-to-play remake of the classic Nintendo game developed by Buziol Games and released for the Windows platform in 2003.

Security researchers have uncovered a bug that could allow attackers to deliver malware directly into employees' Microsoft Teams inbox. "Organisations that use Microsoft Teams inherit Microsoft's default configuration which allows users from outside of their organisation to reach out to their staff members," Jumpsec researcher Max Corbridge explained.
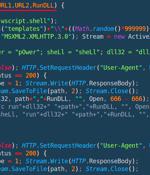
A new strain of JavaScript dropper has been observed delivering next-stage payloads like Bumblebee and IcedID. Cybersecurity firm Deep Instinct is tracking the malware as PindOS, which contains the name in its "User-Agent" string. Both Bumblebee and IcedID serve as loaders, acting as a vector for other malware on compromised hosts, including ransomware.

Malware intended to spread on USB drives is unintentionally infecting networked storage devices, according to infosec vendor Checkpoint. "Upon returning to his home hospital in Europe, the employee introduced the infected USB drive to the hospital's computer systems, which led the infection to spread.".

BlackLotus, the malware capable of bypassing Secure Boot protections and compromising Windows computers, has caught the ire of the NSA, which today published a guide to help organizations detect and prevent infections of the UEFI bootkit. In research published in March, ESET malware analyst Martin Smolár confirmed the myth of an in-the-wild bootkit bypassing Secure Boot "Is now a reality," as opposed to hypothetical threats raised by some experts and the usual slew of fake bootkits criminals attempted to trick fellow miscreants into buying.

Security researchers have found a simple way to deliver malware to an organization with Microsoft Teams, despite restrictions in the application for files from external sources.With 280 million monthly active users, Microsoft Teams has been adopted by organizations as a communication and collaboration platform part of the Microsoft 365 cloud-based services.

The U.S. National Security Agency released today guidance on how to defend against BlackLotus UEFI bootkit malware attacks. In May, Microsoft released security updates to address a Secure Boot zero-day vulnerability that was used to bypass patches released for CVE-2022-21894, the Secure Boot bug initially abused in BlackLotus attacks last year.