Security News

Russian national Vladimir Dunaev has been sentenced to five years and four months in prison for his role in creating and distributing the Trickbot malware used in attacks against hospitals, companies, and individuals worldwide. The initial indictment accused Dunaev and eight co-defendants of engaging in the development, deployment, administration, and financial gains from the Trickbot malware operation.

Cybersecurity researchers have shed light on the command-and-control (C2) server of a known malware family called SystemBC. "SystemBC can be purchased on underground marketplaces and is supplied...
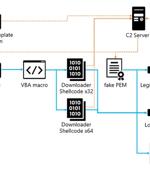
Cybersecurity researchers have uncovered an updated version of a backdoor called LODEINFO that's distributed via spear-phishing attacks. The findings come from Japanese company ITOCHU Cyber &...

ESET researchers have discovered NSPX30, a sophisticated implant used by a new China-aligned APT group, which they dubbed Blackwood. It leverages adversary-in-the-middle techniques to hijack update requests from legitimate software to deliver the implant.

A new Go-based malware loader called CherryLoader has been discovered by threat hunters in the wild to deliver additional payloads onto compromised hosts for follow-on exploitation. Arctic Wolf...

An article published today by the UK National Cyber Security Centre suggests there is a "Realistic possibility" that by 2025, the most sophisticated attackers' tools will improve markedly thanks to AI models informed by data describing successful cyber-hits. At the lower end, cyber criminals who employ social engineering are expected to enjoy a significant boost thanks to the wide-scale uptake of consumer-grade generative AI tools such as ChatGPT, Google Bard, and Microsoft Copilot.
The threat actors behind ClearFake, SocGholish, and dozens of other actors have established partnerships with another entity known as VexTrio as part of a massive "criminal affiliate program," new...

Cracked software have been observed infecting Apple macOS users with a previously undocumented stealer malware capable of harvesting system information and cryptocurrency wallet data. Kaspersky,...

The threat actor tracked as TA866 has resurfaced after a nine-month hiatus with a new large-volume phishing campaign to deliver known malware families such as WasabiSeed and Screenshotter. The...

The Federal Bureau of Investigation and Cybersecurity & Infrastructure Security Agency warned in a joint advisory about a threat actor deploying a botnet that makes use of the Androxgh0st malware. The Androxgh0st malware was exposed in December 2022 by Lacework, a cloud security company.