Security News

A recently disclosed security flaw in OSGeo GeoServer GeoTools has been exploited as part of multiple campaigns to deliver cryptocurrency miners, botnet malware such as Condi and JenX, and a known...

Hackers are targeting other hackers with a fake OnlyFans tool that claims to help steal accounts but instead infects threat actors with the Lumma stealer information-stealing malware. [...]
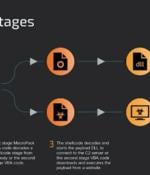
Threat actors are likely employing a tool designated for red teaming exercises to serve malware, according to new findings from Cisco Talos. The program in question is a payload generation...

The Chinese-speaking threat actor known as Earth Lusca has been observed using a new backdoor dubbed KTLVdoor as part of a cyber attack targeting an unnamed trading company based in China. The...

A new malware campaign is spoofing Palo Alto Networks' GlobalProtect VPN software to deliver a variant of the WikiLoader (aka WailingCrab) loader by means of a search engine optimization (SEO)...

GitHub is being abused to distribute the Lumma Stealer information-stealing malware as fake fixes posted in project comments. [...]

A campaign that started on August 5, 2024, is spreading a previously undocumented malware named "Voldemort" to organizations worldwide, impersonating tax agencies from the U.S., Europe, and Asia. [...]

Cybersecurity researchers have uncovered a novel malware campaign that leverages Google Sheets as a command-and-control (C2) mechanism. The activity, detected by Proofpoint starting August 5,...
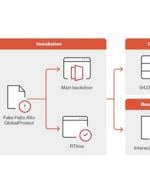
Cybersecurity researchers have disclosed a new campaign that potentially targets users in the Middle East through malware that disguises itself as Palo Alto Networks GlobalProtect virtual private...

The Corona Mirai-based malware botnet is spreading through a 5-year-old remote code execution (RCE) zero-day in AVTECH IP cameras, which have been discontinued for years and will not receive a patch. [...]