Security News

Cybersecurity researchers have discovered the real-world identity of the threat actor behind Golden Chickens malware-as-a-service, who goes by the online persona "Badbullzvenom." The second threat actor, known as Frapstar, is said to identify themselves as "Chuck from Montreal," enabling the cybersecurity firm to piece together the criminal actor's digital footprint.
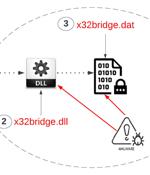
Cybersecurity researchers have uncovered a PlugX sample that employs sneaky methods to infect attached removable USB media devices in order to propagate the malware to additional systems. "This PlugX variant is wormable and infects USB devices in such a way that it conceals itself from the Windows operating file system," Palo Alto Networks Unit 42 researchers Mike Harbison and Jen Miller-Osborn said.

Orcus RAT is a type of malicious software program that enables remote access and control of computers and networks. There are several lifehacks that you should pay attention to while performing the analysis of Orcus RAT. Today we investigate the.

Data compromises steadily increased in the second half of 2022. Data breach notices suddenly lacked details, resulting in increased risk for individuals and businesses, as well as uncertainty about the number of data breaches and victims.

Hackers have leveraged a critical remote code execution vulnerability in Realtek Jungle SDK 134 million attacks trying to infect smart devices in the second half of 2022. Most of these attacks originate from botnet malware families like Mirai, Gafgyt, Mozi, and derivatives of them.

A new Python-based malware has been spotted in the wild featuring remote access trojan capabilities to give its operators control over the breached systems. The PY#RATION malware is distributed via a phishing campaign that uses password-protected ZIP file attachments containing two shortcut.

Organizations in East Asia are being targeted by a likely Chinese-speaking actor dubbed DragonSpark while employing uncommon tactics to go past security layers. "The attacks are characterized by the use of the little known open source SparkRAT and malware that attempts to evade detection through Golang source code interpretation," SentinelOne said in an analysis published today.

The Emotet malware operation has continued to refine its tactics in an effort to fly under the radar, while also acting as a conduit for other dangerous malware such as Bumblebee and IcedID. Emotet, which officially reemerged in late 2021 following a coordinated takedown of its infrastructure by authorities earlier that year, has continued to be a persistent threat that's distributed via phishing emails. With macros becoming an obsolete method of payload distribution and initial infection, the attacks have latched on to other methods to sneak Emotet past malware detection tools.

Microsoft is working on adding XLL add-in protection for Microsoft 365 customers by including automated blocking of all such files downloaded from the Internet. "In order to combat the increasing number of malware attacks in recent months, we are implementing measures that will block XLL add-ins coming from the internet," Redmond says.

Whether an infection is the result of a disgruntled employee, hardware vulnerability, software-based threat, social engineering penetration, robotic attack or human error, all organizations must...