Security News

NET loaders that are highly obfuscated and dropping info-stealer malware. The loaders are distributing the Formbook info-stealing malware collection as part of an ongoing campaign, the researchers write in a report out this week.
Users searching for popular software are being targeted by a new malvertising campaign that abuses Google Ads to serve trojanized variants that deploy malware, such as Raccoon Stealer and Vidar. The activity makes use of seemingly credible websites with typosquatted domain names that are surfaced on top of Google search results in the form of malicious ads by hijacking searches for specific keywords.

A sophisticated and very patient threat group behind a global malvertising scheme is using so-called aged domains to skirt past cybersecurity tools and catch victims in investment scams. Cybercriminals who run malvertising campaigns typically will spin up a domain and quickly put it into use.

The Windows port of ChromeLoader is typically delivered in ISO image files that marks are tricked into downloading, opening, and running the contents of - these ISO files are purported to be installation media for sought-after applications, such as cracked games and software suites. In reality, the image files contain an executable that schedules a PowerShell script that brings up ChromeLoader proper.
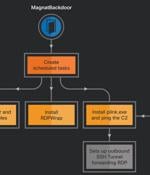
A series of malicious campaigns have been leveraging fake installers of popular apps and games such as Viber, WeChat, NoxPlayer, and Battlefield as a lure to trick users into downloading a new backdoor and an undocumented malicious Google Chrome extension with the goal of stealing credentials and data stored in the compromised systems as well as maintaining persistent remote access. A noteworthy aspect of the intrusions is the use of malvertising as a means to strike individuals who are looking for popular software on search engines to present them links to download fake installers that drop a password stealer called RedLine Stealer, a Chrome extension dubbed "MagnatExtension" that's programmed to record keystrokes and capture screenshots, and an AutoIt-based backdoor that establishes remote access to the machine.
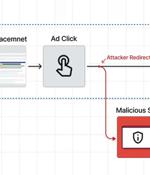
Cybersecurity researchers on Wednesday publicized the disruption of a "Clever" malvertising network targeting AnyDesk that delivered a weaponized installer of the remote desktop software via rogue Google ads that appeared in the search engine results pages. AnyDesk's remote desktop access solution has been downloaded by more than 300 million users worldwide, according to the company's website.

A malvertising operation observed last year by advertising cybersecurity company Confiant exploited what turned out to be a zero-day vulnerability in the WebKit browser engine. Confiant researchers discovered the security hole while analyzing a campaign carried out by a threat actor they call ScamClub.

A recently identified malvertising campaign targeting mobile and other connected devices users makes heavy use of obfuscation and cloaking to avoid detection. Dubbed LuckyBoy, the multi-stage, tag-based campaign is focused on iOS, Android, and Xbox users.

Cloud communications platform as a service company Twilio this week disclosed a security incident that resulted in hackers uploading a modified version of the TaskRouter JS SDK to its site. Designed to provide easy interaction with the Twilio TaskRouter, the SDK was hosted in an Amazon Web Services S3 bucket that was improperly secured, thus becoming accessible to the attackers.

Google has removed 500 Chrome extensions from its online store after researchers found that attackers were using them to steal browser data, according to a new report from security firm Duo Security. In a message to the researchers that it had removed the extensions, Google noted that it "Regularly sweeps to find extensions using similar techniques, code and behaviors and take down those extensions if they violate our policies."