Security News

A supply chain attack involving 21 backdoored Magento extensions has compromised between 500 and 1,000 e-commerce stores, including one belonging to a $40 billion multinational. [...]
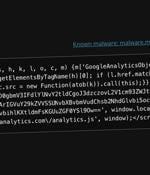
Threat actors have been observed leveraging Google Tag Manager (GTM) to deliver credit card skimmer malware targeting Magento-based e-commerce websites. Website security company Sucuri said the...

Approximately 5% of all Adobe Commerce and Magento online stores, or 4,275 in absolute numbers, have been hacked in "CosmicSting" attacks. [...]

Cybersecurity researchers have disclosed that 5% of all Adobe Commerce and Magento stores have been hacked by malicious actors by exploiting a security vulnerability dubbed CosmicSting. Tracked as...

Threat actors have been observed using swap files in compromised websites to conceal a persistent credit card skimmer and harvest payment information. The sneaky technique, observed by Sucuri on a...
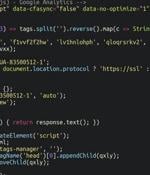
Multiple content management system (CMS) platforms like WordPress, Magento, and OpenCart have been targeted by a new credit card web skimmer called Caesar Cipher Skimmer. A web skimmer refers to...

A vulnerability dubbed "CosmicSting" impacting Adobe Commerce and Magento websites remains largely unpatched nine days after the security update has been made available, leaving millions of sites open to catastrophic attacks. "CosmicSting is the worst bug to hit Magento and Adobe Commerce stores in two years," says Sansec.

Threat actors have been found exploiting a critical flaw in Magento to inject a persistent backdoor into e-commerce websites. The attack leverages CVE-2024-20720 (CVSS score: 9.1), which has been...
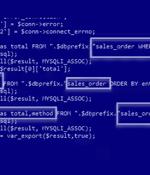
E-commerce sites using Adobe's Magento 2 software are the target of an ongoing campaign that has been active since at least January 2023. The attacks, dubbed Xurum by Akamai, leverage a now-patched critical security flaw in Adobe Commerce and Magento Open Source that, if successfully exploited, could lead to arbitrary code execution.

Ecommerce stores using Adobe's open source Magento 2 software are being targeted by an ongoing exploitation campaign based on a critical vulnerability that was patched last year, on February 13, 2022. "The attacker seems to be interested in payment stats from the orders in the victim's Magento store placed in the past 10 days," they said.